Andrew Watters
A Casual Network Investigation of the Russian Ministry of Defense
Work in progress
Disclaimer: I am not trying to hack anyone here, and I am not affiliated with the U.S. Government. Exploring the defense computer network of a foreign military under these circumstances is very likely to be illegal in Russia. The only reason I am doing this is that I have a clause in my SSH banner warning adversaries not to try to hack me, and the Russians have violated my no-hacking policy on numerous occasions. So I feel like I have license to investigate their capabilities, if for no other reason than to document what they appear to be doing. In any event, do not try this at home.
Skip to 2021 Ukraine intervention section
Skip to 2022 updates and further analysis 
Introduction
After several years of running my own servers, I've gained a fair amount of knowledge of what foreign hackers do. The vast majority of hacking attempts on my servers are brute-force login attempts via SSH. Typically, this involves a random user name, with user names that are not even on my server and that I have no idea why the perpetrator tried. A typical excerpt of my /var/log/secure file follows:
Apr 8 20:19:19 justice sshd[225942]: Invalid user jeff from 134.209.115.206 port 55616
Apr 8 20:19:19 justice sshd[225942]: input_userauth_request: invalid user jeff
Apr 8 20:19:19 justice sshd[225942]: pam_unix(sshd:auth): check pass; user unknown
Apr 8 20:19:19 justice sshd[225942]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=134.209.115.206
Apr 8 20:19:21 justice sshd[225942]: Failed password for invalid user jeff from 134.209.115.206 port 55616 ssh2
Apr 8 20:19:22 justice sshd[225942]: Received disconnect from 134.209.115.206 port 55616:11: Bye Bye
Apr 8 20:19:22 justice sshd[225942]: Disconnected from 134.209.115.206 port 55616
Apr 8 20:19:58 justice sshd[225944]: Invalid user test from 64.227.21.201 port 45962
Apr 8 20:19:58 justice sshd[225944]: input_userauth_request: invalid user test
Apr 8 20:19:58 justice sshd[225944]: pam_unix(sshd:auth): check pass; user unknown
Apr 8 20:19:58 justice sshd[225944]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=64.227.21.201
Apr 8 20:19:59 justice sshd[225944]: Failed password for invalid user test from 64.227.21.201 port 45962 ssh2
Apr 8 20:20:00 justice sshd[225944]: Received disconnect from 64.227.21.201 port 45962:11: Bye Bye
Apr 8 20:20:00 justice sshd[225944]: Disconnected from 64.227.21.201 port 45962
Apr 8 20:20:04 justice sshd[225952]: Invalid user admin from 51.75.25.12 port 45014
Apr 8 20:20:04 justice sshd[225952]: input_userauth_request: invalid user admin
Apr 8 20:20:04 justice sshd[225952]: pam_unix(sshd:auth): check pass; user unknown
Apr 8 20:20:04 justice sshd[225952]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=51.75.25.12
Apr 8 20:20:05 justice sshd[225952]: Failed password for invalid user admin from 51.75.25.12 port 45014 ssh2
Apr 8 20:20:05 justice sshd[225952]: Received disconnect from 51.75.25.12 port 45014:11: Bye Bye
Apr 8 20:20:05 justice sshd[225952]: Disconnected from 51.75.25.12 port 45014
Apr 8 20:21:08 justice sshd[225956]: User root from 45.55.128.109 not allowed because not listed in AllowUsers
Apr 8 20:21:08 justice sshd[225956]: input_userauth_request: invalid user root
Apr 8 20:21:09 justice sshd[225956]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=45.55.128.109 user=root
Apr 8 20:21:09 justice sshd[225956]: pam_succeed_if(sshd:auth): requirement "uid >= 1000" not met by user "root"
Apr 8 20:21:11 justice sshd[225956]: Failed password for invalid user root from 45.55.128.109 port 34020 ssh2
Apr 8 20:21:11 justice sshd[225956]: Received disconnect from 45.55.128.109 port 34020:11: Bye Bye
Apr 8 20:21:11 justice sshd[225956]: Disconnected from 45.55.128.109 port 34020
Apr 8 20:21:12 justice sshd[225957]: Invalid user cactiuser from 192.144.235.246 port 50992
Apr 8 20:21:12 justice sshd[225957]: input_userauth_request: invalid user cactiuser
Apr 8 20:21:12 justice sshd[225957]: pam_unix(sshd:auth): check pass; user unknown
Apr 8 20:21:12 justice sshd[225957]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.144.235.246
Apr 8 20:21:14 justice sshd[225957]: Failed password for invalid user cactiuser from 192.144.235.246 port 50992 ssh2
Apr 8 20:21:14 justice sshd[225957]: Received disconnect from 192.144.235.246 port 50992:11: Bye Bye
Apr 8 20:21:14 justice sshd[225957]: Disconnected from 192.144.235.246 port 50992
It got to a point where there were a quarter million attempts per day-- no joke. I finally got around to installing fail2ban, which is a great stopgap measure. However, even fail2ban isn't perfect; if you set the ban time to something like 100 hours, you get hundreds and hundreds of iptables entries. Maybe not to the point where it would degrade network performance, but if I set the ban time longer and have like 32,000 entries, that is going to be a problem. I'm still exploring solutions in this area and will probably install an actual intrusion prevention system in the future. But I'm not there yet.
This project stemmed from my routine audits of my log files, which clearly show plenty of Russian-controlled IP addresses. Admittedly, it is hard to tell which ones are criminals and which ones, if any, are government-affiliated. After reading an excellent paper on the Russian Ministry of Defense's GRU hacking unit, and having complained numerous times to the FBI about what I feel is unusually high hacking activity from the Russians and Chinese, I decided to simply take matters into my own hands and develop information that might at least lead to an explanation of why I experience this.
The Ministry of Defense public-facing network
The host www.mil.ru resolves to 82.202.189.138 and seemed like the natural starting point. I decided to run a scan of that whole subnet, and I am shocked beyond belief at the following output of nmap:
[root@justice ~]# nmap -Pn -v -sS 82.202.189.1-255
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-08 18:07 PDT
Initiating Parallel DNS resolution of 255 hosts. at 18:07
Completed Parallel DNS resolution of 255 hosts. at 18:07, 0.56s elapsed
Initiating SYN Stealth Scan at 18:07
Scanning 64 hosts [1000 ports/host]
Discovered open port 80/tcp on 82.202.189.19
Discovered open port 80/tcp on 82.202.189.13
Discovered open port 80/tcp on 82.202.189.48
Discovered open port 80/tcp on 82.202.189.17
Discovered open port 80/tcp on 82.202.189.26
Discovered open port 80/tcp on 82.202.189.12
Discovered open port 80/tcp on 82.202.189.16
Discovered open port 80/tcp on 82.202.189.10
Discovered open port 80/tcp on 82.202.189.63
Discovered open port 80/tcp on 82.202.189.14
Discovered open port 80/tcp on 82.202.189.28
Discovered open port 80/tcp on 82.202.189.45
Discovered open port 443/tcp on 82.202.189.12
Discovered open port 443/tcp on 82.202.189.19
Discovered open port 443/tcp on 82.202.189.13
Discovered open port 80/tcp on 82.202.189.57
Discovered open port 80/tcp on 82.202.189.52
Discovered open port 443/tcp on 82.202.189.26
Discovered open port 443/tcp on 82.202.189.17
Discovered open port 443/tcp on 82.202.189.16
Discovered open port 25/tcp on 82.202.189.44
Discovered open port 443/tcp on 82.202.189.45
Discovered open port 443/tcp on 82.202.189.39
Discovered open port 443/tcp on 82.202.189.11
Discovered open port 443/tcp on 82.202.189.14
Discovered open port 443/tcp on 82.202.189.28
Discovered open port 25/tcp on 82.202.189.60
Discovered open port 80/tcp on 82.202.189.59
Discovered open port 443/tcp on 82.202.189.36
Discovered open port 443/tcp on 82.202.189.58
Discovered open port 443/tcp on 82.202.189.15
Discovered open port 587/tcp on 82.202.189.44
Discovered open port 443/tcp on 82.202.189.57
Discovered open port 25/tcp on 82.202.189.20
Discovered open port 587/tcp on 82.202.189.60
Discovered open port 443/tcp on 82.202.189.59
Discovered open port 443/tcp on 82.202.189.22
Discovered open port 443/tcp on 82.202.189.52
Discovered open port 443/tcp on 82.202.189.63
Discovered open port 25/tcp on 82.202.189.43
Discovered open port 443/tcp on 82.202.189.50
Discovered open port 587/tcp on 82.202.189.43
Discovered open port 8080/tcp on 82.202.189.21
Discovered open port 80/tcp on 82.202.189.49
Discovered open port 443/tcp on 82.202.189.49
Stats: 0:00:23 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 5.87% done; ETC: 18:13 (0:05:52 remaining)
Stats: 0:00:27 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 7.06% done; ETC: 18:13 (0:05:55 remaining)
Discovered open port 2875/tcp on 82.202.189.40
Discovered open port 1011/tcp on 82.202.189.40
Discovered open port 1011/tcp on 82.202.189.41
Discovered open port 481/tcp on 82.202.189.40
Discovered open port 49161/tcp on 82.202.189.40
Discovered open port 1583/tcp on 82.202.189.40
Discovered open port 24/tcp on 82.202.189.40
Discovered open port 2605/tcp on 82.202.189.40
Discovered open port 1023/tcp on 82.202.189.40
Discovered open port 9090/tcp on 82.202.189.40
Discovered open port 8333/tcp on 82.202.189.40
Discovered open port 5811/tcp on 82.202.189.40
Discovered open port 1097/tcp on 82.202.189.40
Discovered open port 512/tcp on 82.202.189.40
Discovered open port 3322/tcp on 82.202.189.40
Discovered open port 20000/tcp on 82.202.189.40
Discovered open port 513/tcp on 82.202.189.40
Discovered open port 3659/tcp on 82.202.189.40
Discovered open port 9110/tcp on 82.202.189.40
Discovered open port 9220/tcp on 82.202.189.40
Discovered open port 3889/tcp on 82.202.189.40
Discovered open port 1080/tcp on 82.202.189.40
Discovered open port 2126/tcp on 82.202.189.40
Discovered open port 3007/tcp on 82.202.189.40
Discovered open port 10616/tcp on 82.202.189.40
Discovered open port 1044/tcp on 82.202.189.40
Discovered open port 1130/tcp on 82.202.189.40
Discovered open port 6547/tcp on 82.202.189.40
Discovered open port 5190/tcp on 82.202.189.40
Discovered open port 6692/tcp on 82.202.189.40
Discovered open port 3283/tcp on 82.202.189.40
Discovered open port 6106/tcp on 82.202.189.40
Discovered open port 1183/tcp on 82.202.189.40
Discovered open port 8654/tcp on 82.202.189.40
Discovered open port 1783/tcp on 82.202.189.40
Discovered open port 1131/tcp on 82.202.189.40
Discovered open port 49155/tcp on 82.202.189.40
Discovered open port 3306/tcp on 82.202.189.40
Discovered open port 8080/tcp on 82.202.189.40
Discovered open port 5900/tcp on 82.202.189.40
Discovered open port 111/tcp on 82.202.189.40
Discovered open port 587/tcp on 82.202.189.40
Discovered open port 23/tcp on 82.202.189.40
Discovered open port 143/tcp on 82.202.189.40
Discovered open port 443/tcp on 82.202.189.40
Discovered open port 256/tcp on 82.202.189.40
Discovered open port 25/tcp on 82.202.189.40
Discovered open port 445/tcp on 82.202.189.40
Discovered open port 554/tcp on 82.202.189.40
Discovered open port 80/tcp on 82.202.189.40
Discovered open port 481/tcp on 82.202.189.41
Discovered open port 139/tcp on 82.202.189.40
Discovered open port 2875/tcp on 82.202.189.41
Discovered open port 3389/tcp on 82.202.189.40
Discovered open port 8888/tcp on 82.202.189.40
Discovered open port 110/tcp on 82.202.189.40
Discovered open port 135/tcp on 82.202.189.40
Discovered open port 993/tcp on 82.202.189.40
Discovered open port 21/tcp on 82.202.189.40
Discovered open port 49161/tcp on 82.202.189.41
Discovered open port 24/tcp on 82.202.189.41
Discovered open port 1023/tcp on 82.202.189.41
Discovered open port 1583/tcp on 82.202.189.41
Discovered open port 5811/tcp on 82.202.189.41
Discovered open port 2605/tcp on 82.202.189.41
Discovered open port 9090/tcp on 82.202.189.41
Discovered open port 8333/tcp on 82.202.189.41
Discovered open port 1097/tcp on 82.202.189.41
Discovered open port 20000/tcp on 82.202.189.41
Discovered open port 512/tcp on 82.202.189.41
Discovered open port 3322/tcp on 82.202.189.41
Discovered open port 513/tcp on 82.202.189.41
Discovered open port 9110/tcp on 82.202.189.41
Discovered open port 9220/tcp on 82.202.189.41
Discovered open port 3659/tcp on 82.202.189.41
Discovered open port 1080/tcp on 82.202.189.41
Discovered open port 1130/tcp on 82.202.189.41
Discovered open port 3889/tcp on 82.202.189.41
Discovered open port 2126/tcp on 82.202.189.41
Discovered open port 10616/tcp on 82.202.189.41
Discovered open port 1044/tcp on 82.202.189.41
Discovered open port 6547/tcp on 82.202.189.41
Discovered open port 5190/tcp on 82.202.189.41
Discovered open port 6106/tcp on 82.202.189.41
Discovered open port 1183/tcp on 82.202.189.41
Discovered open port 3283/tcp on 82.202.189.41
Discovered open port 6692/tcp on 82.202.189.41
Discovered open port 1783/tcp on 82.202.189.41
Discovered open port 113/tcp on 82.202.189.40
Discovered open port 1025/tcp on 82.202.189.40
Discovered open port 199/tcp on 82.202.189.40
Discovered open port 1720/tcp on 82.202.189.40
Discovered open port 22/tcp on 82.202.189.40
Discovered open port 995/tcp on 82.202.189.40
Discovered open port 1723/tcp on 82.202.189.40
Discovered open port 53/tcp on 82.202.189.40
Discovered open port 3306/tcp on 82.202.189.41
Discovered open port 8080/tcp on 82.202.189.41
Discovered open port 5900/tcp on 82.202.189.41
Discovered open port 111/tcp on 82.202.189.41
Discovered open port 143/tcp on 82.202.189.41
Discovered open port 23/tcp on 82.202.189.41
Discovered open port 1131/tcp on 82.202.189.41
Discovered open port 8654/tcp on 82.202.189.41
Discovered open port 49155/tcp on 82.202.189.41
Discovered open port 587/tcp on 82.202.189.41
Discovered open port 25/tcp on 82.202.189.41
Discovered open port 256/tcp on 82.202.189.41
Discovered open port 445/tcp on 82.202.189.41
Discovered open port 443/tcp on 82.202.189.41
Discovered open port 110/tcp on 82.202.189.41
Increasing send delay for 82.202.189.41 from 0 to 5 due to max_successful_tryno increase to 4
Discovered open port 135/tcp on 82.202.189.41
Discovered open port 3389/tcp on 82.202.189.41
Discovered open port 139/tcp on 82.202.189.41
Discovered open port 113/tcp on 82.202.189.41
Discovered open port 993/tcp on 82.202.189.41
Discovered open port 21/tcp on 82.202.189.41
Discovered open port 53/tcp on 82.202.189.41
Discovered open port 22/tcp on 82.202.189.41
Discovered open port 1720/tcp on 82.202.189.41
Discovered open port 1723/tcp on 82.202.189.41
Discovered open port 1025/tcp on 82.202.189.41
Discovered open port 995/tcp on 82.202.189.41
Discovered open port 8031/tcp on 82.202.189.41
Discovered open port 8088/tcp on 82.202.189.41
Discovered open port 1700/tcp on 82.202.189.41
Discovered open port 11111/tcp on 82.202.189.41
Increasing send delay for 82.202.189.41 from 5 to 10 due to 11 out of 19 dropped probes since last increase.
Discovered open port 9898/tcp on 82.202.189.41
Discovered open port 1277/tcp on 82.202.189.41
Discovered open port 3986/tcp on 82.202.189.41
SYN Stealth Scan Timing: About 9.25% done; ETC: 18:17 (0:09:19 remaining)
Increasing send delay for 82.202.189.41 from 10 to 20 due to 11 out of 12 dropped probes since last increase.
Stats: 0:01:22 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 12.03% done; ETC: 18:18 (0:09:52 remaining)
Increasing send delay for 82.202.189.40 from 0 to 5 due to 25 out of 81 dropped probes since last increase.
Increasing send delay for 82.202.189.41 from 20 to 40 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 82.202.189.40 from 5 to 10 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 82.202.189.41 from 40 to 80 due to 11 out of 11 dropped probes since last increase.
Stats: 0:03:06 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 23.60% done; ETC: 18:20 (0:09:59 remaining)
Increasing send delay for 82.202.189.41 from 80 to 160 due to 11 out of 11 dropped probes since last increase.
Stats: 0:03:17 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 24.76% done; ETC: 18:20 (0:09:56 remaining)
Increasing send delay for 82.202.189.40 from 10 to 20 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 82.202.189.41 from 160 to 320 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 82.202.189.40 from 20 to 40 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 32.81% done; ETC: 18:20 (0:09:15 remaining)
Increasing send delay for 82.202.189.41 from 320 to 640 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 82.202.189.40 from 40 to 80 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 37.51% done; ETC: 18:20 (0:08:31 remaining)
Increasing send delay for 82.202.189.40 from 80 to 160 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 43.74% done; ETC: 18:20 (0:07:48 remaining)
Increasing send delay for 82.202.189.40 from 160 to 320 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 82.202.189.41 from 640 to 1000 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 48.85% done; ETC: 18:20 (0:07:05 remaining)
Discovered open port 8081/tcp on 82.202.189.52
Increasing send delay for 82.202.189.40 from 320 to 640 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 54.30% done; ETC: 18:20 (0:06:20 remaining)
Completed SYN Stealth Scan against 82.202.189.42 in 471.41s (63 hosts left)
SYN Stealth Scan Timing: About 59.47% done; ETC: 18:20 (0:05:28 remaining)
SYN Stealth Scan Timing: About 64.26% done; ETC: 18:20 (0:04:46 remaining)
Discovered open port 465/tcp on 82.202.189.43
Increasing send delay for 82.202.189.40 from 640 to 1000 due to 11 out of 11 dropped probes since last increase.
Discovered open port 8181/tcp on 82.202.189.52
SYN Stealth Scan Timing: About 69.18% done; ETC: 18:20 (0:04:04 remaining)
Discovered open port 465/tcp on 82.202.189.60
Discovered open port 9091/tcp on 82.202.189.58
SYN Stealth Scan Timing: About 75.13% done; ETC: 18:19 (0:03:11 remaining)
Completed SYN Stealth Scan against 82.202.189.43 in 615.39s (62 hosts left)
SYN Stealth Scan Timing: About 80.51% done; ETC: 18:19 (0:02:30 remaining)
Stats: 0:10:34 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 83.24% done; ETC: 18:19 (0:02:07 remaining)
Discovered open port 81/tcp on 82.202.189.52
SYN Stealth Scan Timing: About 89.10% done; ETC: 18:19 (0:01:21 remaining)
Completed SYN Stealth Scan against 82.202.189.15 in 670.63s (61 hosts left)
Completed SYN Stealth Scan against 82.202.189.8 in 676.67s (60 hosts left)
Completed SYN Stealth Scan against 82.202.189.16 in 677.15s (59 hosts left)
Stats: 0:11:22 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 92.52% done; ETC: 18:19 (0:00:55 remaining)
Completed SYN Stealth Scan against 82.202.189.24 in 684.19s (58 hosts left)
Completed SYN Stealth Scan against 82.202.189.20 in 688.00s (57 hosts left)
Completed SYN Stealth Scan against 82.202.189.23 in 691.09s (56 hosts left)
Completed SYN Stealth Scan against 82.202.189.1 in 691.23s (55 hosts left)
Completed SYN Stealth Scan against 82.202.189.11 in 691.24s (54 hosts left)
Completed SYN Stealth Scan against 82.202.189.5 in 692.22s (53 hosts left)
Completed SYN Stealth Scan against 82.202.189.17 in 692.42s (52 hosts left)
Completed SYN Stealth Scan against 82.202.189.21 in 692.54s (51 hosts left)
Completed SYN Stealth Scan against 82.202.189.47 in 692.55s (50 hosts left)
Completed SYN Stealth Scan against 82.202.189.26 in 693.29s (49 hosts left)
Completed SYN Stealth Scan against 82.202.189.29 in 693.89s (48 hosts left)
Completed SYN Stealth Scan against 82.202.189.14 in 694.93s (47 hosts left)
Completed SYN Stealth Scan against 82.202.189.19 in 695.34s (46 hosts left)
Completed SYN Stealth Scan against 82.202.189.57 in 697.52s (45 hosts left)
Completed SYN Stealth Scan against 82.202.189.28 in 698.75s (44 hosts left)
Completed SYN Stealth Scan against 82.202.189.12 in 698.99s (43 hosts left)
Completed SYN Stealth Scan against 82.202.189.33 in 700.20s (42 hosts left)
Completed SYN Stealth Scan against 82.202.189.45 in 700.41s (41 hosts left)
Completed SYN Stealth Scan against 82.202.189.30 in 701.16s (40 hosts left)
Completed SYN Stealth Scan against 82.202.189.9 in 701.57s (39 hosts left)
Completed SYN Stealth Scan against 82.202.189.7 in 701.78s (38 hosts left)
Completed SYN Stealth Scan against 82.202.189.61 in 703.04s (37 hosts left)
Completed SYN Stealth Scan against 82.202.189.50 in 704.35s (36 hosts left)
Completed SYN Stealth Scan against 82.202.189.10 in 707.77s (35 hosts left)
Completed SYN Stealth Scan against 82.202.189.60 in 707.97s (34 hosts left)
Completed SYN Stealth Scan against 82.202.189.6 in 708.00s (33 hosts left)
Completed SYN Stealth Scan against 82.202.189.27 in 708.21s (32 hosts left)
Completed SYN Stealth Scan against 82.202.189.44 in 708.40s (31 hosts left)
Completed SYN Stealth Scan against 82.202.189.18 in 708.56s (30 hosts left)
Completed SYN Stealth Scan against 82.202.189.53 in 708.59s (29 hosts left)
Completed SYN Stealth Scan against 82.202.189.13 in 709.66s (28 hosts left)
Completed SYN Stealth Scan against 82.202.189.32 in 709.89s (27 hosts left)
Completed SYN Stealth Scan against 82.202.189.31 in 710.47s (26 hosts left)
Completed SYN Stealth Scan against 82.202.189.22 in 710.61s (25 hosts left)
Completed SYN Stealth Scan against 82.202.189.4 in 711.00s (24 hosts left)
Completed SYN Stealth Scan against 82.202.189.64 in 711.01s (23 hosts left)
Completed SYN Stealth Scan against 82.202.189.55 in 711.20s (22 hosts left)
Completed SYN Stealth Scan against 82.202.189.36 in 711.22s (21 hosts left)
Completed SYN Stealth Scan against 82.202.189.51 in 711.42s (20 hosts left)
Completed SYN Stealth Scan against 82.202.189.37 in 712.60s (19 hosts left)
Completed SYN Stealth Scan against 82.202.189.2 in 712.82s (18 hosts left)
Completed SYN Stealth Scan against 82.202.189.58 in 713.25s (17 hosts left)
Completed SYN Stealth Scan against 82.202.189.25 in 713.44s (16 hosts left)
Completed SYN Stealth Scan against 82.202.189.34 in 713.64s (15 hosts left)
Completed SYN Stealth Scan against 82.202.189.46 in 713.76s (14 hosts left)
Completed SYN Stealth Scan against 82.202.189.48 in 713.80s (13 hosts left)
Completed SYN Stealth Scan against 82.202.189.56 in 714.47s (12 hosts left)
Completed SYN Stealth Scan against 82.202.189.39 in 715.80s (11 hosts left)
Completed SYN Stealth Scan against 82.202.189.52 in 715.94s (10 hosts left)
Completed SYN Stealth Scan against 82.202.189.54 in 716.23s (9 hosts left)
Completed SYN Stealth Scan against 82.202.189.38 in 716.45s (8 hosts left)
Completed SYN Stealth Scan against 82.202.189.49 in 716.63s (7 hosts left)
Completed SYN Stealth Scan against 82.202.189.59 in 716.69s (6 hosts left)
Completed SYN Stealth Scan against 82.202.189.63 in 716.84s (5 hosts left)
Completed SYN Stealth Scan against 82.202.189.62 in 716.87s (4 hosts left)
Completed SYN Stealth Scan against 82.202.189.3 in 716.90s (3 hosts left)
Completed SYN Stealth Scan against 82.202.189.35 in 717.01s (2 hosts left)
Stats: 0:12:04 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 97.81% done; ETC: 18:19 (0:00:16 remaining)
Stats: 0:12:15 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 97.82% done; ETC: 18:19 (0:00:16 remaining)
Stats: 0:12:18 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 97.82% done; ETC: 18:19 (0:00:16 remaining)
Stats: 0:12:53 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 97.84% done; ETC: 18:20 (0:00:17 remaining)
Stats: 0:13:35 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 97.86% done; ETC: 18:20 (0:00:18 remaining)
Stats: 0:16:57 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 97.96% done; ETC: 18:24 (0:00:21 remaining)
Stats: 0:18:02 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.00% done; ETC: 18:25 (0:00:22 remaining)
Stats: 0:18:37 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.02% done; ETC: 18:26 (0:00:23 remaining)
Stats: 0:20:42 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.08% done; ETC: 18:28 (0:00:24 remaining)
Stats: 0:20:49 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.08% done; ETC: 18:28 (0:00:24 remaining)
Stats: 0:24:52 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.21% done; ETC: 18:32 (0:00:27 remaining)
Stats: 0:25:01 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.22% done; ETC: 18:32 (0:00:27 remaining)
Stats: 0:25:39 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.23% done; ETC: 18:33 (0:00:28 remaining)
Stats: 0:25:56 elapsed; 0 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 98.24% done; ETC: 18:33 (0:00:28 remaining)
[root@justice ~]#
What does it mean? A few initial observations:
- There are a ton of servers on this subnet with open ports (64).
- Two of those servers (.40 and .41) appear to be seriously important, and those two are dropping SYN packets and causing my scan to hang indefinitely.
- It should not take 25 minutes to scan one subnet, and I interrupted this scan because it was taking too long-- so I didn't even get to the main webserver at .138 in the automated portion.
- The Ministry of Defense seems to have kept current on the proceedings of IETF, such as this article on SYN dropping.
I targeted 82.202.189.40 but came up empty with an initial quick scan, even with a one second send delay between SYN packets:
[root@justice ~]# nmap -v -sS -Pn --scan-delay 1s 82.202.189.40
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-09 08:19 PDT
Initiating Parallel DNS resolution of 1 host. at 08:19
Completed Parallel DNS resolution of 1 host. at 08:19, 0.00s elapsed
Initiating SYN Stealth Scan at 08:19
Scanning 82.202.189.40 [1000 ports]
SYN Stealth Scan Timing: About 1.50% done; ETC: 08:54 (0:33:56 remaining)
SYN Stealth Scan Timing: About 4.50% done; ETC: 08:53 (0:32:11 remaining)
SYN Stealth Scan Timing: About 9.55% done; ETC: 08:53 (0:30:28 remaining)
SYN Stealth Scan Timing: About 14.35% done; ETC: 08:53 (0:28:45 remaining)
Stats: 0:06:11 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 18.45% done; ETC: 08:53 (0:27:24 remaining)
SYN Stealth Scan Timing: About 23.30% done; ETC: 08:53 (0:25:41 remaining)
SYN Stealth Scan Timing: About 28.25% done; ETC: 08:53 (0:24:00 remaining)
SYN Stealth Scan Timing: About 33.35% done; ETC: 08:53 (0:22:17 remaining)
SYN Stealth Scan Timing: About 38.45% done; ETC: 08:53 (0:20:34 remaining)
SYN Stealth Scan Timing: About 43.90% done; ETC: 08:53 (0:18:51 remaining)
SYN Stealth Scan Timing: About 49.60% done; ETC: 08:53 (0:17:07 remaining)
SYN Stealth Scan Timing: About 54.95% done; ETC: 08:53 (0:15:25 remaining)
SYN Stealth Scan Timing: About 60.25% done; ETC: 08:54 (0:13:41 remaining)
SYN Stealth Scan Timing: About 65.45% done; ETC: 08:54 (0:11:57 remaining)
SYN Stealth Scan Timing: About 70.75% done; ETC: 08:54 (0:10:10 remaining)
SYN Stealth Scan Timing: About 75.95% done; ETC: 08:54 (0:08:23 remaining)
SYN Stealth Scan Timing: About 81.10% done; ETC: 08:54 (0:06:37 remaining)
SYN Stealth Scan Timing: About 86.25% done; ETC: 08:54 (0:04:50 remaining)
SYN Stealth Scan Timing: About 91.30% done; ETC: 08:54 (0:03:04 remaining)
SYN Stealth Scan Timing: About 96.40% done; ETC: 08:54 (0:01:16 remaining)
Completed SYN Stealth Scan at 08:54, 2119.58s elapsed (1000 total ports)
Nmap scan report for 82.202.189.40
Host is up (0.22s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE
55055/tcp closed unknown
55056/tcp closed unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 2119.66 seconds
Raw packets sent: 2117 (93.148KB) | Rcvd: 2216 (88.640KB)
This is probably the big one...the earlier scans revealed an open Telnet port:
[root@justice ~]# nmap -v -sS -Pn --scan-delay 1s -p 23 82.202.189.40
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-09 09:02 PDT
Initiating Parallel DNS resolution of 1 host. at 09:02
Completed Parallel DNS resolution of 1 host. at 09:02, 0.00s elapsed
Initiating SYN Stealth Scan at 09:02
Scanning 82.202.189.40 [1 port]
Completed SYN Stealth Scan at 09:02, 3.00s elapsed (1 total ports)
Nmap scan report for 82.202.189.40
Host is up.
PORT STATE SERVICE
23/tcp filtered telnet
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 3.10 seconds
Raw packets sent: 2 (88B) | Rcvd: 0 (0B)
[root@justice ~]# nmap -v -sY -Pn --scan-delay 1s -p 23 82.202.189.40
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-09 09:09 PDT
Initiating Parallel DNS resolution of 1 host. at 09:09
Completed Parallel DNS resolution of 1 host. at 09:09, 0.00s elapsed
Initiating SCTP INIT Scan at 09:09
Scanning 82.202.189.40 [1 port]
Completed SCTP INIT Scan at 09:09, 3.00s elapsed (1 total ports)
Nmap scan report for 82.202.189.40
Host is up.
PORT STATE SERVICE
23/sctp filtered unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 3.10 seconds
Raw packets sent: 2 (104B) | Rcvd: 0 (0B)
[root@justice ~]# nmap -v -sS -Pn --scan-delay 2s -p 23 -f 82.202.189.40
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-09 09:12 PDT
Initiating Parallel DNS resolution of 1 host. at 09:12
Completed Parallel DNS resolution of 1 host. at 09:12, 0.00s elapsed
Initiating SYN Stealth Scan at 09:12
Scanning 82.202.189.40 [1 port]
Completed SYN Stealth Scan at 09:12, 6.01s elapsed (1 total ports)
Nmap scan report for 82.202.189.40
Host is up.
PORT STATE SERVICE
23/tcp filtered telnet
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 6.09 seconds
Raw packets sent: 2 (88B) | Rcvd: 0 (0B)
There's no way it would be that easy. This must be a honeypot...will return with a more carefully crafted scan in the near future. Meanwhile, there is other stuff to do.
Check this out-- the Ministry of Defense is running their .40 server through Kaspersky! Laughing out loud at that.
[root@justice ~]# nmap -A -vv -sS -Pn --scan-delay 2s -p 23 -f 82.202.189.40
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-09 09:35 PDT
NSE: Loaded 110 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
NSE: Starting runlevel 2 (of 2) scan.
Initiating Parallel DNS resolution of 1 host. at 09:35
Completed Parallel DNS resolution of 1 host. at 09:35, 1.28s elapsed
Initiating SYN Stealth Scan at 09:35
Scanning 82.202.189.40 [1 port]
Completed SYN Stealth Scan at 09:35, 6.01s elapsed (1 total ports)
Initiating Service scan at 09:35
Initiating OS detection (try #1) against 82.202.189.40
Retrying OS detection (try #2) against 82.202.189.40
Initiating Traceroute at 09:37
Completed Traceroute at 09:39, 124.01s elapsed
Initiating Parallel DNS resolution of 14 hosts. at 09:39
Completed Parallel DNS resolution of 14 hosts. at 09:39, 1.11s elapsed
NSE: Script scanning 82.202.189.40.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:39
Completed NSE at 09:39, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Nmap scan report for 82.202.189.40
Host is up.
Scanned at 2020-04-09 09:35:42 PDT for 231s
PORT STATE SERVICE VERSION
23/tcp filtered telnet
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: storage-misc|firewall|general purpose|broadband router
Running (JUST GUESSING): Sun embedded (87%), Linux 2.6.X (86%), Cyberoam embedded (85%)
OS CPE: cpe:/h:sun:storedge_3310_fc_array cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:2.6.18
OS fingerprint not ideal because: Scan delay (2000) is greater than 500
Aggressive OS guesses: Sun StorEdge 3310 FC storage array (87%), Sun StorEdge 3510 FC storage array (87%), Endian Firewall 2.3 (Linux 2.6) (86%), Linux 2.6.18 (86%), Linux 2.6.23 (86%), Linux 2.6.24 (86%), Linux 2.6.32 (86%), Cyberoam UTM firewall (85%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=6.40%E=4%D=4/9%OT=%CT=%CU=%PV=N%G=N%TM=5E8F4FC5%P=x86_64-redhat-linux-gnu)
T5(R=Y%DF=Y%TG=40%W=0%S=Z%A=Z%F=R%O=%RD=0%Q=)
U1(R=N)
IE(R=N)
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 0.09 ms slash.slash.law (192.168.1.1)
2 0.82 ms 206.81.106.145
3 0.76 ms 23.136.224.141
4 0.65 ms 23.136.224.154
5 1.71 ms xe-0-5-0-2-3.r05.plalca01.us.bb.gin.ntt.net (129.250.201.213)
6 155.80 ms ae-15.r01.snjsca04.us.bb.gin.ntt.net (129.250.5.33)
7 2.53 ms ae-1.r22.snjsca04.us.bb.gin.ntt.net (129.250.3.26)
8 64.59 ms ae-7.r23.asbnva02.us.bb.gin.ntt.net (129.250.6.238)
9 67.16 ms ae-0.r22.asbnva02.us.bb.gin.ntt.net (129.250.3.84)
10 147.70 ms ae-16.r21.frnkge13.de.bb.gin.ntt.net (129.250.4.97)
11 150.13 ms ae-5.r00.frnkge07.de.bb.gin.ntt.net (129.250.4.185)
12 156.21 ms ae-2.a00.frnkge07.de.bb.gin.ntt.net (129.250.4.237)
13 150.25 ms trans-telecom-0.a00.frnkge07.de.bb.gin.ntt.net (213.198.82.158)
14 ...
15 194.28 ms Kaspersky-gw.transtelecom.net (188.43.25.125)
16 ... 30
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
NSE: Starting runlevel 2 (of 2) scan.
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 232.51 seconds
Raw packets sent: 112 (8.496KB) | Rcvd: 109 (7.662KB)
Of course, telnetting to 82.202.189.40:23 does not work. Must not be a honeypot after all (lol).
I then ran curl on each IP address on this subnet just to see how each web-accessible server would respond. Check out this badass shell script (based on this answer on Stack Exchange) that executes curl on an entire subnet and saves the output in a text file:
for i in {1..255}; do
echo "curl http://82.202.189.$i/..."
curl --connect-timeout 3 -vs "http://82.202.189.$i/" >> foo
echo "success!"
done
curl http://82.202.189.19/...
* About to connect() to 82.202.189.19 port 80 (#0)
* Trying 82.202.189.19...
* Connected to 82.202.189.19 (82.202.189.19) port 80 (#0)
> GET / HTTP/1.1
> User-Agent: curl/7.29.0
> Host: 82.202.189.19
> Accept: */*
>
< HTTP/1.1 301 Moved Permanently
< Server: nginx/1.17.5
< Date: Thu, 09 Apr 2020 04:00:10 GMT
< Content-Type: text/html
< Content-Length: 169
< Connection: keep-alive
< Location: https://82.202.189.19/
<
{ [data not shown]
* Connection #0 to host 82.202.189.19 left intact
success!
curl http://82.202.189.20/...
* About to connect() to 82.202.189.20 port 80 (#0)
* Trying 82.202.189.20...
* Connection refused
* Failed connect to 82.202.189.20:80; Connection refused
* Closing connection 0
success!
curl http://82.202.189.21/...
* About to connect() to 82.202.189.21 port 80 (#0)
* Trying 82.202.189.21...
* Connection refused
* Failed connect to 82.202.189.21:80; Connection refused
* Closing connection 0
success!
curl http://82.202.189.22/...
* About to connect() to 82.202.189.22 port 80 (#0)
* Trying 82.202.189.22...
* Connection refused
* Failed connect to 82.202.189.22:80; Connection refused
* Closing connection 0
success!
curl http://82.202.189.23/...
* About to connect() to 82.202.189.23 port 80 (#0)
* Trying 82.202.189.23...
* Connection timed out after 3001 milliseconds
* Closing connection 0
success!
curl http://82.202.189.24/...
* About to connect() to 82.202.189.24 port 80 (#0)
* Trying 82.202.189.24...
* Connection timed out after 3001 milliseconds
* Closing connection 0
success!
curl http://82.202.189.25/...
* About to connect() to 82.202.189.25 port 80 (#0)
* Trying 82.202.189.25...
* Connection timed out after 3001 milliseconds
* Closing connection 0
success!
curl http://82.202.189.26/...
* About to connect() to 82.202.189.26 port 80 (#0)
* Trying 82.202.189.26...
* Connected to 82.202.189.26 (82.202.189.26) port 80 (#0)
> GET / HTTP/1.1
> User-Agent: curl/7.29.0
> Host: 82.202.189.26
> Accept: */*
>
< HTTP/1.1 301 Moved Permanently
< Server: nginx/1.15.7
< Date: Thu, 09 Apr 2020 04:00:20 GMT
< Content-Type: text/html
< Content-Length: 169
< Connection: keep-alive
< Location: https://82.202.189.26/
<
{ [data not shown]
* Connection #0 to host 82.202.189.26 left intact
success!
I got as far as .198 with curl before it froze and would not proceed; I figure I got enough by that point anyway, so I didn't push it. My full results are available here; the file starts with the raw output of the script before I interrupted it, and then has the raw HTML (sorry, I didn't think to print telemetry or a legend/key on this first attempt). As you can see, there are a ton of active web servers on this subnet, many of which returned significant amounts of configuration information. Interesting to see Microsoft IIS being used in what must be a crazy-harsh environment, which was unexpected.
To be continued
Step Two: Who is Hacking me?
A random audit of /var/log/secure reveals the following list of unique IP addresses that have attempted to hack me in the last few days via SSH brute force attacks:
101.36.177.242
101.50.126.96
101.91.238.160
102.65.169.135
102.65.174.235
103.108.144.245
103.108.87.187
103.115.104.229
103.1.209.245
103.212.211.164
103.215.139.101
103.23.102.3
103.26.40.145
103.40.241.14
103.45.102.212
103.54.36.50
103.56.79.2
103.57.123.1
103.60.214.110
103.92.31.75
104.131.138.126
104.198.16.231
104.236.125.98
104.236.52.94
104.248.121.67
104.248.237.238
106.12.106.42
106.12.106.78
106.12.108.170
106.12.119.1
106.12.162.201
106.12.163.87
106.12.179.56
106.12.185.54
106.12.192.201
106.12.193.217
106.12.194.204
106.12.208.118
106.12.222.209
106.12.23.198
106.12.69.68
106.12.71.159
106.12.80.138
106.12.88.165
106.13.123.73
106.13.1.245
106.13.128.64
106.13.129.119
106.13.136.3
106.13.139.26
106.13.140.107
106.13.144.78
106.13.15.153
106.13.167.77
106.13.179.152
106.13.181.89
106.13.187.114
106.13.211.155
106.13.213.177
106.13.233.186
106.13.28.108
106.13.38.246
106.13.41.71
106.13.47.68
106.13.52.234
106.13.55.50
106.13.78.120
106.13.80.186
106.13.84.151
106.13.88.108
106.13.88.196
106.13.88.44
106.13.99.51
106.38.33.70
106.39.31.93
106.52.102.190
106.52.19.71
106.52.234.191
106.52.50.225
106.53.72.83
106.54.141.45
106.54.235.94
106.54.237.74
106.54.25.220
106.75.174.87
106.75.176.189
107.170.149.126
108.34.248.130
109.194.174.78
110.188.22.8
110.52.140.106
110.93.200.118
111.10.43.201
111.229.103.45
111.229.106.118
111.229.110.107
111.229.115.117
111.229.116.147
111.229.116.240
111.229.126.37
111.229.188.102
111.229.205.95
111.229.28.34
111.230.10.176
111.230.13.11
111.230.209.68
111.231.69.222
111.231.75.5
111.231.93.242
111.231.94.138
111.67.193.176
111.67.199.136
112.13.198.138
112.21.191.252
112.215.113.10
112.35.0.252
113.116.49.190
113.125.118.93
113.125.120.149
113.140.80.174
113.204.205.66
114.243.231.136
114.67.101.203
114.67.123.3
114.67.74.139
114.67.75.133
114.67.79.46
114.67.81.251
115.159.149.136
115.159.51.239
115.220.3.88
115.238.228.149
116.12.251.135
116.196.107.128
116.90.81.15
117.34.200.242
118.101.192.81
118.24.104.55
118.24.108.205
118.24.14.64
118.24.158.42
118.24.236.121
118.24.30.97
118.24.82.81
118.25.220.142
118.25.54.60
118.25.74.248
118.25.94.105
118.89.108.152
118.89.111.225
118.89.60.105
119.29.129.88
119.29.140.241
119.29.161.236
119.29.199.150
119.29.246.210
1.193.160.164
119.44.20.30
119.57.247.86
119.96.222.202
120.133.1.16
120.194.108.100
120.28.167.33
1.203.115.141
120.70.100.159
120.88.46.226
120.92.114.71
120.92.34.203
120.92.45.102
121.229.26.104
121.237.171.177
1.214.215.236
1.214.245.27
121.54.169.127
121.69.135.162
122.114.209.239
122.14.195.58
122.152.204.42
122.152.217.9
122.155.204.128
122.192.255.228
122.226.135.93
122.51.167.200
122.51.217.131
122.51.241.12
122.51.41.44
122.51.50.210
122.51.67.249
122.51.91.131
123.122.126.54
123.206.174.21
123.206.36.174
123.207.250.132
123.207.33.139
123.212.255.193
123.7.63.49
124.109.24.60
124.117.250.190
124.156.107.252
124.160.83.138
124.207.165.138
124.235.206.130
124.65.18.102
125.124.43.25
125.33.25.6
125.64.94.220
125.75.4.83
125.91.105.108
125.91.109.126
128.106.195.126
128.199.116.10
128.199.174.201
128.199.204.26
129.204.139.26
129.204.181.118
129.211.24.187
129.28.191.55
130.185.155.34
131.221.80.177
132.232.37.63
132.232.90.20
13.235.128.36
134.175.178.118
134.209.250.9
137.74.132.171
138.197.158.118
138.197.180.102
138.255.148.35
138.68.226.234
13.90.170.53
139.155.118.190
139.155.20.146
139.155.70.21
139.155.71.154
139.155.86.144
139.162.75.112
139.198.121.63
139.199.104.217
139.199.168.18
139.199.32.57
139.199.4.219
139.199.98.175
139.215.217.181
139.59.46.243
139.59.90.31
139.99.236.133
140.143.226.19
140.143.228.18
140.143.236.54
140.143.250.57
140.143.58.46
140.143.9.142
140.238.145.45
140.246.175.68
14.116.208.72
14.116.216.176
141.255.165.126
14.18.58.216
14.215.44.9
14.29.130.153
14.29.145.11
14.29.148.201
14.29.165.173
14.29.184.152
14.29.214.233
142.93.150.6
144.22.108.33
144.91.97.233
145.239.91.88
146.164.36.34
147.135.153.116
148.215.18.103
148.70.159.5
148.70.178.70
148.70.195.54
148.70.68.175
149.56.15.98
149.56.44.101
150.109.104.117
150.109.126.175
150.109.47.167
151.80.141.109
151.80.60.151
152.136.152.220
157.230.113.218
157.230.249.90
157.230.251.115
158.69.110.31
158.69.192.35
158.69.70.163
159.203.73.181
159.65.132.92
159.65.196.65
162.243.128.30
162.243.129.134
162.243.131.164
162.243.132.150
162.243.133.180
162.243.133.49
162.243.55.188
162.243.74.129
163.172.160.152
163.172.247.10
163.172.49.56
163.179.126.39
163.44.148.143
164.132.54.215
164.52.24.164
164.68.112.178
165.22.110.2
165.227.125.156
165.227.55.56
166.141.71.101
167.172.114.165
168.90.88.50
1.71.129.49
171.34.173.49
174.135.156.170
175.106.17.235
175.140.138.193
175.140.8.246
175.24.18.86
176.31.127.152
177.139.194.62
177.141.123.20
177.23.184.99
177.43.236.178
177.85.118.70
177.85.93.198
178.128.13.87
178.128.162.10
178.128.57.147
178.128.59.109
178.128.83.204
178.128.95.85
178.149.114.79
178.176.30.211
178.33.66.88
178.73.215.171
180.150.187.159
180.150.189.206
180.166.184.66
180.76.105.165
180.76.110.70
180.76.111.214
180.76.147.221
180.76.171.57
180.76.173.191
180.76.176.113
180.76.176.174
180.76.238.183
181.143.10.148
181.30.28.247
182.208.248.211
182.23.3.162
182.23.82.18
182.43.165.158
182.43.215.50
182.61.104.246
182.61.12.58
182.61.3.152
182.61.46.187
182.74.133.117
182.74.25.246
183.12.240.248
183.61.109.23
185.123.164.52
185.202.1.85
185.6.172.152
185.81.99.206
187.12.167.85
187.180.64.39
187.202.72.172
188.127.192.119
188.166.164.10
188.166.5.36
188.170.13.225
188.219.251.4
188.254.0.2
188.35.187.50
189.210.177.177
190.117.62.241
190.12.66.27
190.13.145.60
190.194.111.141
190.210.42.209
190.85.34.203
191.234.161.50
191.234.189.22
191.8.187.245
192.144.132.172
192.144.155.63
192.144.161.40
192.144.232.101
192.144.235.246
192.207.202.2
192.228.100.11
192.228.100.200
192.241.231.79
192.241.235.76
192.241.237.148
192.241.239.192
192.241.249.53
192.99.244.225
193.112.123.100
193.112.219.207
193.112.42.13
193.148.69.157
196.52.43.60
197.214.64.230
198.100.146.67
198.108.66.32
198.199.124.109
198.49.73.13
200.137.5.196
200.146.215.26
200.209.145.251
200.209.174.38
200.37.97.194
201.163.180.183
201.193.82.10
201.49.110.210
202.147.198.154
202.168.205.181
202.175.46.170
202.43.164.162
202.79.168.211
203.130.192.243
203.177.71.254
203.81.78.180
206.189.156.42
206.189.84.108
207.154.193.178
207.248.127.161
208.88.172.135
210.13.96.74
210.202.8.64
211.169.249.156
211.169.249.231
211.197.251.121
211.20.181.186
211.234.119.189
211.24.110.125
2.119.3.137
212.129.245.105
212.204.65.160
212.237.58.119
212.64.54.49
212.64.71.132
212.83.183.57
213.141.132.29
213.21.53.2
213.32.67.160
217.146.86.154
217.182.67.242
217.182.70.150
217.77.221.85
218.200.235.178
218.36.86.40
218.76.54.205
218.78.54.80
218.89.241.68
219.153.100.153
220.133.95.68
220.133.97.20
220.166.63.47
220.167.224.133
221.140.151.235
221.219.212.170
221.6.105.62
222.128.20.226
222.186.15.246
222.186.52.78
222.222.31.70
222.232.29.235
222.73.129.15
222.73.62.184
222.79.184.36
223.247.129.7
23.239.19.234
27.154.58.154
34.92.104.164
34.92.175.197
35.196.8.137
35.200.183.13
35.222.59.60
35.231.211.161
35.231.214.101
36.110.78.62
36.156.155.192
36.159.109.30
36.189.255.162
37.152.177.25
37.187.69.69
37.252.187.140
37.252.189.70
37.2.9.207
37.59.123.166
41.111.135.199
41.59.82.183
41.63.0.133
41.77.146.98
42.101.44.158
42.3.63.92
43.226.149.148
43.226.149.84
43.240.125.195
45.119.80.39
45.132.16.61
45.164.8.244
45.225.216.80
45.249.94.170
45.4.5.221
45.55.128.109
45.55.173.225
45.88.13.159
45.95.168.145
45.95.168.59
46.101.209.178
46.175.21.30
46.182.19.49
46.41.151.138
47.241.74.30
47.44.215.186
49.232.141.44
49.232.156.177
49.232.165.42
49.232.173.147
49.232.64.41
49.233.202.149
49.233.202.62
49.233.208.40
49.233.75.234
49.233.87.107
49.234.10.207
49.234.113.133
49.234.196.225
49.234.222.209
49.234.23.248
49.234.233.164
49.234.43.39
49.234.54.58
49.235.139.216
49.235.144.143
49.235.161.88
49.235.190.177
49.235.216.107
49.235.23.20
49.235.242.163
49.235.76.84
49.235.91.83
49.235.93.12
49.235.93.192
49.235.94.172
49.235.97.29
49.51.171.154
49.7.14.184
49.72.212.22
51.158.108.186
51.159.35.94
51.178.30.102
5.135.158.228
51.38.121.207
51.38.186.47
51.38.188.101
51.38.51.200
51.68.229.73
51.75.126.115
51.75.24.200
51.75.25.12
51.77.150.203
51.77.212.179
51.77.212.235
51.79.44.52
51.83.45.93
51.83.74.126
51.91.102.173
51.91.108.98
51.91.251.20
5.196.229.117
5.196.7.123
52.172.221.28
52.183.21.61
5.39.88.60
54.37.14.3
54.37.158.218
54.37.20.138
54.38.242.233
54.38.53.251
58.210.82.250
58.250.86.44
59.148.173.231
59.36.75.227
59.58.173.41
60.2.10.190
60.51.17.33
61.133.133.207
61.151.130.20
61.222.56.80
61.250.122.115
61.28.108.122
61.74.118.139
61.93.201.198
61.94.212.4
62.210.110.192
62.234.156.221
62.234.187.137
62.234.91.204
62.234.97.45
65.49.20.67
65.49.20.68
65.49.20.69
66.154.107.47
66.70.130.149
67.205.135.127
68.183.146.178
68.183.35.255
69.229.6.2
69.55.55.155
71.189.47.10
71.246.210.34
71.62.129.30
74.208.235.29
77.46.239.41
77.65.79.150
78.134.90.84
78.217.177.232
78.42.135.89
79.173.253.50
80.21.147.85
80.211.79.220
80.211.88.70
80.211.9.57
80.80.214.195
80.82.70.118
80.84.146.20
80.98.249.181
81.4.100.188
81.84.249.147
82.208.133.133
82.251.161.207
82.78.193.249
85.143.216.214
85.186.38.228
86.111.95.131
86.21.205.149
88.88.254.93
89.248.174.3
91.121.175.61
91.121.211.34
91.121.221.195
91.144.173.197
91.233.42.38
91.237.25.28
92.118.161.1
92.222.75.80
92.222.94.46
92.33.153.202
94.177.216.68
94.181.51.245
94.191.120.108
94.191.15.40
94.191.24.214
94.191.40.166
94.254.125.44
95.216.94.220
95.85.12.122
96.93.196.89
A whois on each of these reveals around 10-15 IP addresses that trace to Russia (output here), of which the following is a sample:
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '109.194.168.0 - 109.194.175.255'
% Abuse contact for '109.194.168.0 - 109.194.175.255' is 'abuse@domru.ru'
inetnum: 109.194.168.0 - 109.194.175.255
netname: ERTH-TMN-PPPOE-22-NET
descr: CJSC "ER-Telecom Holding" Tyumen' branch
descr: Tyumen', Russia
descr: PPPoE Individual customers
country: RU
admin-c: NOCC2-RIPE
org: ORG-CHTb1-RIPE
tech-c: NOCC2-RIPE
status: ASSIGNED PA
mnt-by: RAID-MNT
remarks: INFRA-AW
created: 2012-10-24T14:41:57Z
last-modified: 2013-02-05T03:58:50Z
source: RIPE
organisation: ORG-CHTb1-RIPE
org-name: JSC "ER-Telecom Holding" Tyumen' branch
org-type: OTHER
descr: TM DOM.RU, Tyumen' ISP
address: Permyakova str., 7/1
address: Tyumen', Russia, 625013
phone: +7 (3452) 51-41-31
fax-no: +7 (3452) 51-41-31
admin-c: NOCC2-RIPE
tech-c: NOCC2-RIPE
[...]
There are also entire networks of servers constantly port scanning me, such as 84.17.0.0/16 and 82.148.0.0/16 (both are Russian-owned according to whois information). It got to the point where I had to block those entire networks (65,536 IP addresses) in my firewall. These guys are not giving up: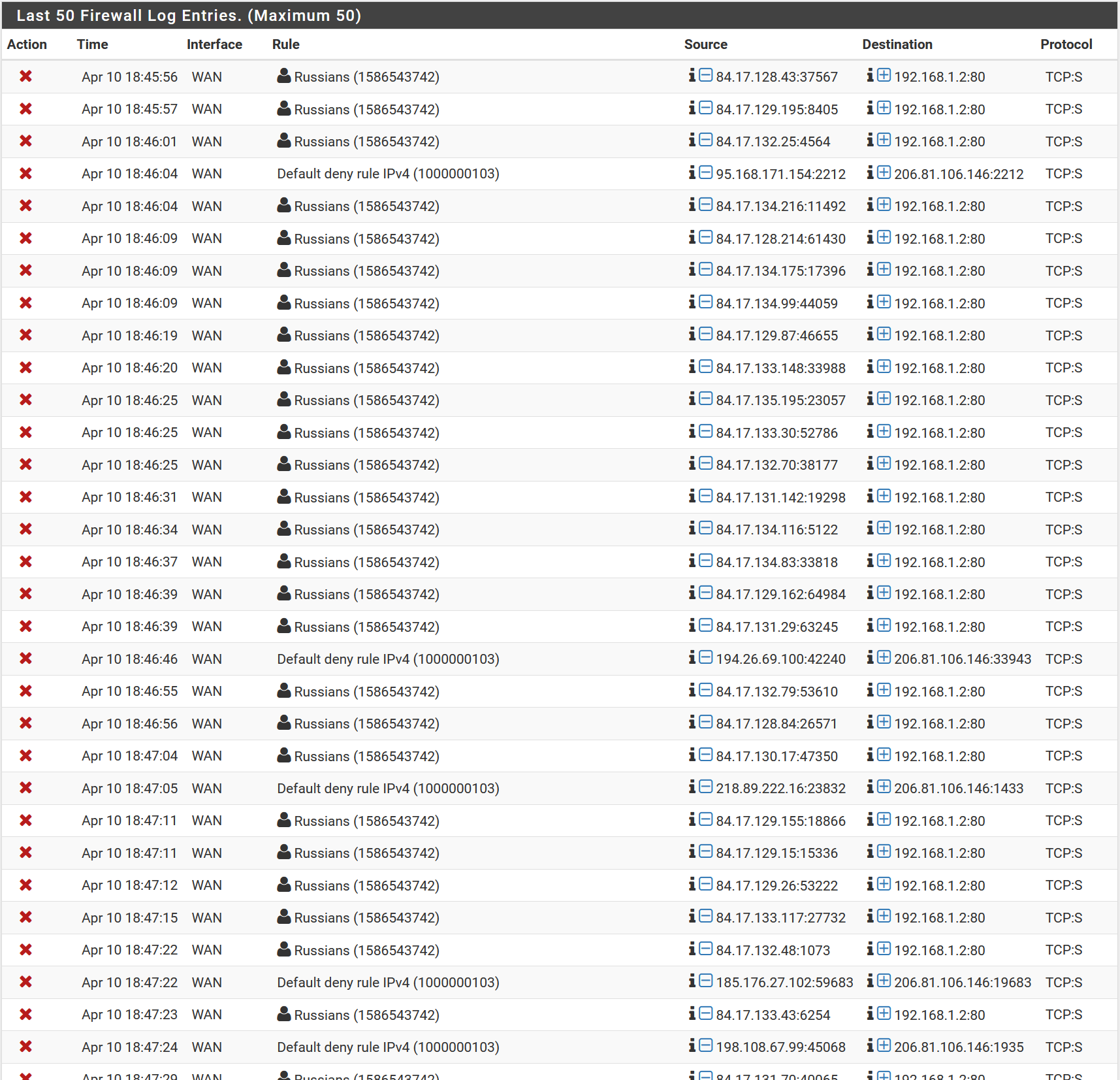
When I nmap them back, I get some interesting results:
[root@justice ~]# nmap -A -vv -sS -Pn -f 84.17.129.215
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-10 11:53 PDT
NSE: Loaded 110 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
NSE: Starting runlevel 2 (of 2) scan.
Initiating Parallel DNS resolution of 1 host. at 11:53
Completed Parallel DNS resolution of 1 host. at 11:53, 0.31s elapsed
Initiating SYN Stealth Scan at 11:53
Scanning 215.cust-B32.waldc.net (84.17.129.215) [1000 ports]
Discovered open port 443/tcp on 84.17.129.215
Discovered open port 80/tcp on 84.17.129.215
Completed SYN Stealth Scan at 11:53, 31.81s elapsed (1000 total ports)
Initiating Service scan at 11:53
Scanning 2 services on 215.cust-B32.waldc.net (84.17.129.215)
Completed Service scan at 11:54, 27.74s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 215.cust-B32.waldc.net (84.17.129.215)
Initiating Traceroute at 11:54
Completed Traceroute at 11:54, 3.03s elapsed
Initiating Parallel DNS resolution of 13 hosts. at 11:54
Completed Parallel DNS resolution of 13 hosts. at 11:54, 0.87s elapsed
NSE: Script scanning 84.17.129.215.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:54
NSE Timing: About 79.17% done; ETC: 11:54 (0:00:08 remaining)
NSE Timing: About 87.50% done; ETC: 11:55 (0:00:09 remaining)
NSE Timing: About 91.67% done; ETC: 11:55 (0:00:08 remaining)
NSE Timing: About 95.83% done; ETC: 11:56 (0:00:05 remaining)
Completed NSE at 11:56, 130.75s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Nmap scan report for 215.cust-B32.waldc.net (84.17.129.215)
Host is up (0.18s latency).
Scanned at 2020-04-10 11:53:02 PDT for 198s
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.15 ((CentOS))
|_http-favicon: Unknown favicon MD5: 18946584351D0EC2FE154B5CEDBCEB9F
|_http-methods: No Allow or Public header in OPTIONS response (status code 302)
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Did not follow redirect to http://215.cust-B32.waldc.net/login
443/tcp open ssl/https?
| http-robots.txt: 1 disallowed entry
|_/
| ssl-cert: Subject: commonName=www2.quasys.com/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--/localityName=SomeCity/emailAddress=root@www2.quasys.com/organizationalUnitName=SomeOrganizationalUnit
| Issuer: commonName=www2.quasys.com/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--/localityName=SomeCity/emailAddress=root@www2.quasys.com/organizationalUnitName=SomeOrganizationalUnit
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2012-11-05T09:40:53+00:00
| Not valid after: 2013-11-05T09:40:53+00:00
| MD5: a3ad c09e ea87 04ac 3fe8 2047 f5e4 a5ad
| SHA-1: 8583 0a3c b6cf 1b58 e55b 73fd 325f f836 9a26 6fd7
| -----BEGIN CERTIFICATE-----
| MIIDJzCCApCgAwIBAgICUdswDQYJKoZIhvcNAQEFBQAwga8xCzAJBgNVBAYTAi0t
| MRIwEAYDVQQIDAlTb21lU3RhdGUxETAPBgNVBAcMCFNvbWVDaXR5MRkwFwYDVQQK
| DBBTb21lT3JnYW5pemF0aW9uMR8wHQYDVQQLDBZTb21lT3JnYW5pemF0aW9uYWxV
| bml0MRgwFgYDVQQDDA93d3cyLnF1YXN5cy5jb20xIzAhBgkqhkiG9w0BCQEWFHJv
| b3RAd3d3Mi5xdWFzeXMuY29tMB4XDTEyMTEwNTA5NDA1M1oXDTEzMTEwNTA5NDA1
| M1owga8xCzAJBgNVBAYTAi0tMRIwEAYDVQQIDAlTb21lU3RhdGUxETAPBgNVBAcM
| CFNvbWVDaXR5MRkwFwYDVQQKDBBTb21lT3JnYW5pemF0aW9uMR8wHQYDVQQLDBZT
| b21lT3JnYW5pemF0aW9uYWxVbml0MRgwFgYDVQQDDA93d3cyLnF1YXN5cy5jb20x
| IzAhBgkqhkiG9w0BCQEWFHJvb3RAd3d3Mi5xdWFzeXMuY29tMIGfMA0GCSqGSIb3
| DQEBAQUAA4GNADCBiQKBgQDN1RUlbkUwPXw7kRpAaTunR5c73qnaRVjTfEtKh4bi
| Sdt5uaRIHytxaka3n3p7Kmnxb375Ng+xY7pewgczFAyEPLs9NYLRnr3D1TCz7wTd
| eWSvJy961S7IfzKRjgtRFSNC+/2cWsYu/vQZ3MToMX6ds80dNehLesgi5p1YrETy
| iwIDAQABo1AwTjAdBgNVHQ4EFgQUivS5Dy2QcgASAwN55B2WPWEIMqEwHwYDVR0j
| BBgwFoAUivS5Dy2QcgASAwN55B2WPWEIMqEwDAYDVR0TBAUwAwEB/zANBgkqhkiG
| 9w0BAQUFAAOBgQC5dDc9IbmR6P6TszA83djJL7DH5Pzbz/nExnMAa3CtrnOWTyvX
| vhP2LrRSaXbQrKOqkoE3A89Ne1dLB5BAl8CIfaAB2fGDbJSCmaWx93F3uu0JRKHM
| Wx5fNI9zLNlrWXWCpHl6wlJtvUmmD55hM+XzroEYHlJTlhMu688T9jYXsw==
|_-----END CERTIFICATE-----
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 2.6.39, Linux 2.6.38, Linux 3.2 - 3.6
TCP/IP fingerprint:
OS:SCAN(V=6.40%E=4%D=4/10%OT=80%CT=%CU=%PV=N%DS=18%DC=T%G=N%TM=5E90C154%P=x
OS:86_64-redhat-linux-gnu)ECN(R=Y%DF=Y%TG=40%W=3908%O=M5B4NNSNW7%CC=Y%Q=)T1
OS:(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=N)U1(R=N)IE(R=N
OS:)
Network Distance: 18 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 0.08 ms slash.slash.law (192.168.1.1)
2 0.82 ms 206.81.106.145
3 0.95 ms 23.136.224.141
4 0.93 ms 23.136.224.154
5 1.59 ms xe-0-5-0-2-3.r05.plalca01.us.bb.gin.ntt.net (129.250.201.213)
6 2.67 ms ae-15.r01.snjsca04.us.bb.gin.ntt.net (129.250.5.33)
7 2.31 ms sjo-b21-link.telia.net (62.115.12.52)
8 ...
9 153.56 ms ldn-bb3-link.telia.net (62.115.113.21)
10 148.35 ms adm-bb3-link.telia.net (213.155.136.99)
11 147.93 ms adm-b1-link.telia.net (62.115.137.65)
12 147.81 ms hurricane-109025-adm-b5.c.telia.net (213.248.72.146)
13 155.22 ms 100ge5-1.core1.bru1.he.net (184.104.193.154)
14 ... 17
18 178.71 ms 215.cust-B32.waldc.net (84.17.129.215)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
NSE: Starting runlevel 2 (of 2) scan.
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 199.29 seconds
Raw packets sent: 3054 (137.224KB) | Rcvd: 82 (5.920KB)
Interesting that the SSL certificate was created in November 2012 and has not been updated since it expired in 2013. Can I prove that these IP's belong to the Russian government? No, I can't. But it makes no sense that some random internet consumer in Russia or a data center operator in Belgium has an interest in hacking my server. And this is just the last few days...if I go from a typical sized log file covering a couple weeks, I get a much fuller picture of hacking efforts, of which the following list is a sample of only SSH attacks:
89.38.150.200
89.40.114.6
89.45.45.178
89.46.65.62
90.180.92.121
90.188.15.141
90.22.147.194
90.3.112.119
90.84.41.240
91.103.27.235
91.106.195.180
91.108.155.43
91.114.44.62
91.121.104.181
91.121.116.65
91.121.145.227
91.121.164.188
91.121.175.138
91.121.221.195
91.121.29.57
91.132.0.203
91.144.173.197
91.200.100.19
91.204.188.50
91.205.185.118
91.209.235.28
91.213.77.203
91.218.67.171
91.74.234.154
92.118.160.29
92.118.189.18
92.207.180.50
92.222.89.7
92.252.243.190
92.253.171.172
92.50.249.166
92.62.131.124
93.170.36.5
93.174.93.114
93.174.95.42
93.207.108.143
93.243.141.217
93.4.196.233
94.131.243.73
94.177.214.200
94.177.215.195
94.177.246.39
94.180.58.238
94.181.181.120
94.191.25.32
94.191.76.167
94.191.83.93
94.191.85.216
94.191.90.117
94.191.90.85
94.191.9.85
94.193.38.209
94.228.182.244
94.23.212.137
94.232.136.126
94.23.58.228
94.254.125.44
94.43.85.6
95.110.201.243
95.110.235.17
95.111.74.98
95.130.181.11
95.163.118.126
95.167.225.81
95.181.131.153
95.242.59.150
95.255.14.141
95.48.54.106
95.55.220.226
95.78.176.107
95.78.251.116
95.88.128.23
96.27.249.5
96.78.175.33
96.92.113.85
98.110.74.69
99.108.141.4
[...]
The interesting thing is something I expected: there are plenty of IP blocks that repeat, as if the perpetrators have access to a wide range of IP addresses or servers from which to execute attacks. I probably shouldn't abuse the whois servers, so I held off on whois lookups of these 2,500 IP's. But cross referencing this list with the latest log shows that at least 118 of the "repeat customers" are seriously persistent in the SSH attacks:
103.108.144.245
103.108.87.187
103.215.139.101
104.131.138.126
106.12.80.138
106.13.1.245
106.13.128.64
106.13.213.177
106.13.52.234
106.13.78.120
106.38.33.70
110.93.200.118
111.229.110.107
111.229.126.37
111.229.188.102
111.230.209.68
111.231.69.222
112.21.191.252
113.125.120.149
114.67.79.46
114.67.81.251
115.220.3.88
116.90.81.15
118.24.108.205
118.24.236.121
118.89.108.152
119.29.129.88
120.92.114.71
122.192.255.228
122.51.241.12
123.206.36.174
123.212.255.193
124.117.250.190
124.207.165.138
125.91.105.108
129.28.191.55
139.155.118.190
139.162.75.112
139.59.90.31
139.99.236.133
145.239.91.88
148.70.178.70
148.70.195.54
158.69.70.163
162.243.133.49
165.22.110.2
165.227.125.156
168.90.88.50
1.71.129.49
177.141.123.20
177.23.184.99
178.128.59.109
178.33.66.88
178.73.215.171
180.150.189.206
180.76.105.165
180.76.171.57
180.76.176.113
180.76.238.183
182.61.104.246
182.74.25.246
185.123.164.52
188.170.13.225
188.35.187.50
192.144.161.40
192.228.100.11
192.228.100.200
192.241.231.79
200.209.174.38
201.193.82.10
201.49.110.210
202.147.198.154
202.175.46.170
210.202.8.64
211.169.249.156
212.204.65.160
218.78.54.80
221.140.151.235
222.186.52.78
35.196.8.137
36.110.78.62
37.252.187.140
41.59.82.183
42.101.44.158
43.240.125.195
45.225.216.80
45.55.128.109
45.55.173.225
49.232.156.177
49.233.75.234
49.234.43.39
49.235.144.143
49.235.94.172
49.7.14.184
50.250.237.226
51.158.108.186
5.135.158.228
51.75.25.12
51.77.150.203
51.79.44.52
51.83.45.93
51.91.102.173
61.28.108.122
65.49.20.67
65.49.20.68
65.49.20.69
67.205.135.127
69.229.6.2
69.55.55.155
74.208.235.29
78.217.177.232
80.211.9.57
80.82.70.118
81.4.100.188
86.111.95.131
91.121.221.195
91.144.173.197
94.254.125.44
Doing a whois on each of these is more manageable, and I came up with the following Russians who just will not give up trying to hack me:
source: APNIC
% This query was served by the APNIC Whois Service version 1.88.15-47 (WHOIS-US3)
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '185.123.164.0 - 185.123.167.255'
% Abuse contact for '185.123.164.0 - 185.123.167.255' is 'ru.boscom@inbox.ru'
inetnum: 185.123.164.0 - 185.123.167.255
netname: RU-BOSCOMLLC-20151027
country: RU
org: ORG-BL234-RIPE
admin-c: AL13356-RIPE
tech-c: AL13356-RIPE
status: ALLOCATED PA
mnt-by: RIPE-NCC-HM-MNT
mnt-by: ru-boscomllc-1-mnt
mnt-routes: ru-boscomllc-1-mnt
created: 2015-10-27T14:49:31Z
last-modified: 2018-11-19T13:02:03Z
source: RIPE
organisation: ORG-BL234-RIPE
org-name: Boscom LLC
org-type: LIR
address: Razyezzhaya st., n.5, office 131
address: 191002
address: Saint Petersburg
address: RUSSIAN FEDERATION
admin-c: AL13356-RIPE
tech-c: AL13356-RIPE
--
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '188.170.0.0 - 188.170.31.255'
% Abuse contact for '188.170.0.0 - 188.170.31.255' is 'abuse-mailbox@megafon.ru'
inetnum: 188.170.0.0 - 188.170.31.255
netname: MF-MOSCOW-BBA-POOL-188-170-0
descr: MF-GNOC-STF-20161028
descr: Megafon-Moscow Broadband clients
descr: Moscow Branch of OJSC MegaFon
country: RU
status: ASSIGNED PA
admin-c: MFMS-RIPE
tech-c: MFMS-RIPE
mnt-by: MEGAFON-RIPE-MNT
mnt-lower: MEGAFON-AUTO-MNT
mnt-lower: MF-MOSCOW-MNT
mnt-routes: MF-MOSCOW-MNT
mnt-domains: MF-MOSCOW-MNT
created: 2016-10-28T11:30:44Z
last-modified: 2019-11-29T11:41:45Z
source: RIPE
role: Moscow Branch of PJSC MegaFon Internet Center
address: 41 Oruzheyniy lane, Moscow, Russia, 127006
admin-c: IK9000-RIPE
admin-c: MFON-RIPE
tech-c: IK9000-RIPE
tech-c: MFON-RIPE
nic-hdl: MFMS-RIPE
mnt-by: MF-MOSCOW-MNT
--
% This query was served by the RIPE Database Query Service version 1.97 (WAGYU)
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '188.35.184.0 - 188.35.187.255'
% Abuse contact for '188.35.184.0 - 188.35.187.255' is 'abuse@netorn.net'
inetnum: 188.35.184.0 - 188.35.187.255
netname: NETORN-NET
descr: Netorn, hosting & colocation
country: RU
admin-c: VF64-RIPE
tech-c: AN2262-RIPE
status: ASSIGNED PA
mnt-by: NETORN-MNT
created: 2013-02-18T10:21:10Z
last-modified: 2013-02-19T09:29:23Z
source: RIPE
person: Alexsandr Nechitaylo
address: Netorn LLC
address: 9, Hibinskiy pr.
address: Moscow, Russia, 129336
phone: +7 495 266 6188
fax-no: +7 495 266 2101
nic-hdl: AN2262-RIPE
mnt-by: NETORN-MNT
created: 2006-05-02T10:07:30Z
last-modified: 2006-05-02T10:11:27Z
source: RIPE # Filtered
--
% This query was served by the RIPE Database Query Service version 1.97 (BLAARKOP)
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '91.144.172.0 - 91.144.175.255'
% Abuse contact for '91.144.172.0 - 91.144.175.255' is 'abuse@domru.ru'
inetnum: 91.144.172.0 - 91.144.175.255
netname: ERTH-KIROV2-NET
descr: ZAO "Company "ER-Telecom" Kirov address space
country: RU
admin-c: NOCC1-RIPE
org: ORG-CHKB3-RIPE
tech-c: NOCC1-RIPE
status: ASSIGNED PA
mnt-by: RAID-MNT
created: 2007-10-10T04:13:03Z
last-modified: 2011-01-19T19:02:24Z
source: RIPE
organisation: ORG-CHKB3-RIPE
org-name: JSC "ER-Telecom Holding" Kirov Branch
org-type: OTHER
descr: TM DOM.RU, Kirov ISP
address: Gertsena, 1
address: Kirov, Russia, 610002
phone: +7 (8332) 711-555
fax-no: +7 (8332) 711-555
admin-c: NOCC1-RIPE
tech-c: NOCC1-RIPE
mnt-ref: RAID-MNT
[...]
These entities are present in the older logs as well as the latest logs. I would classify them as persistent threats, though I can't prove they are connected to the Russian government, so I cannot call them Advanced Persistent Threats yet. Cross referencing the IP's in my persistent threat list with a U.S. CISA report from 2016 on Grizzly Steppe revealed no matches; of course, the IP addresses have likely been shut down for years. I'm still working on cross referencing with known Fancy Bear activity. I also installed the geoip utility so I can quickly geolocate IP's moving forward.
To be continued
Conclusion
What does this have to do with my original project? I'm still figuring out whether there is a connection between Russian defense activity and the continuous hacking attempts on my server. I will continue to monitor my logs to see if any interesting IP's pop up. I also continue to report foreign hacking efforts to law enforcement. Meanwhile, any readers who recognize the above IP addresses or whois information should email me details (email here). I'm also open to suggestions and ideas.
Update 12/18/2020: I continue to experience higher than normal levels of hacking attempts. The closest anyone has gotten to hacking me was someone in Europe guessing my username and attempting SSH manually just enough times and just infrequently enough to not trigger fail2ban. This happened in May 2020, shortly after I posted this web page. Coincidence? I don't know, it seems awfully coincidental. I discovered this in an audit of my logs after noticing a "failed login" message in my message of the day, which practically never happens because my username is a made-up word (lol). So yeah, that was an APT. By the way, I do intend to finish this project, I just have not had time due to my work load.
Update 4/1/2021: in case anyone cares, this is by far the most popular page on my website. I've received more than 100,000 visitors in the last year from all over the world, which is embarrassing because I'm not even done with this yet and I originally put it up as a sort-of complaint/joke about the hacking efforts. Thank you for your interest, and as a result of that I need to step up my game here.
Russia's 2021 Ukraine Intervention -- added April 22, 2021
This is a civilian cyber investigation into the anticipated Russian intervention in Ukraine in 2021. Stay tuned as events unfold.
I started this sub-project when it became clear that Russia would be re-entering Ukraine in April/May 2021. This fascinating Google Trends page shows that users in Washington, D.C. started blowing up Google on this topic in late March 2021, several weeks before it was in the mainstream news. Check out the same search trends page viewed from Ukraine. It appears that people in the Karkhiv area are the most concerned about invasion, probably because they are sitting ducks and the Russians could split Eastern Ukraine nearly in half at the Dnieper River if they launch through Karkhiv. Also, there happens to be a major internet exchange in Karkhiv, whose website is hacked, by the way (there are a couple others too, conveniently Russian-owned). This interactive map of Russian military forces shows about 120 tanks and 140 armored personnel carriers practically on the Ukraine border in this region: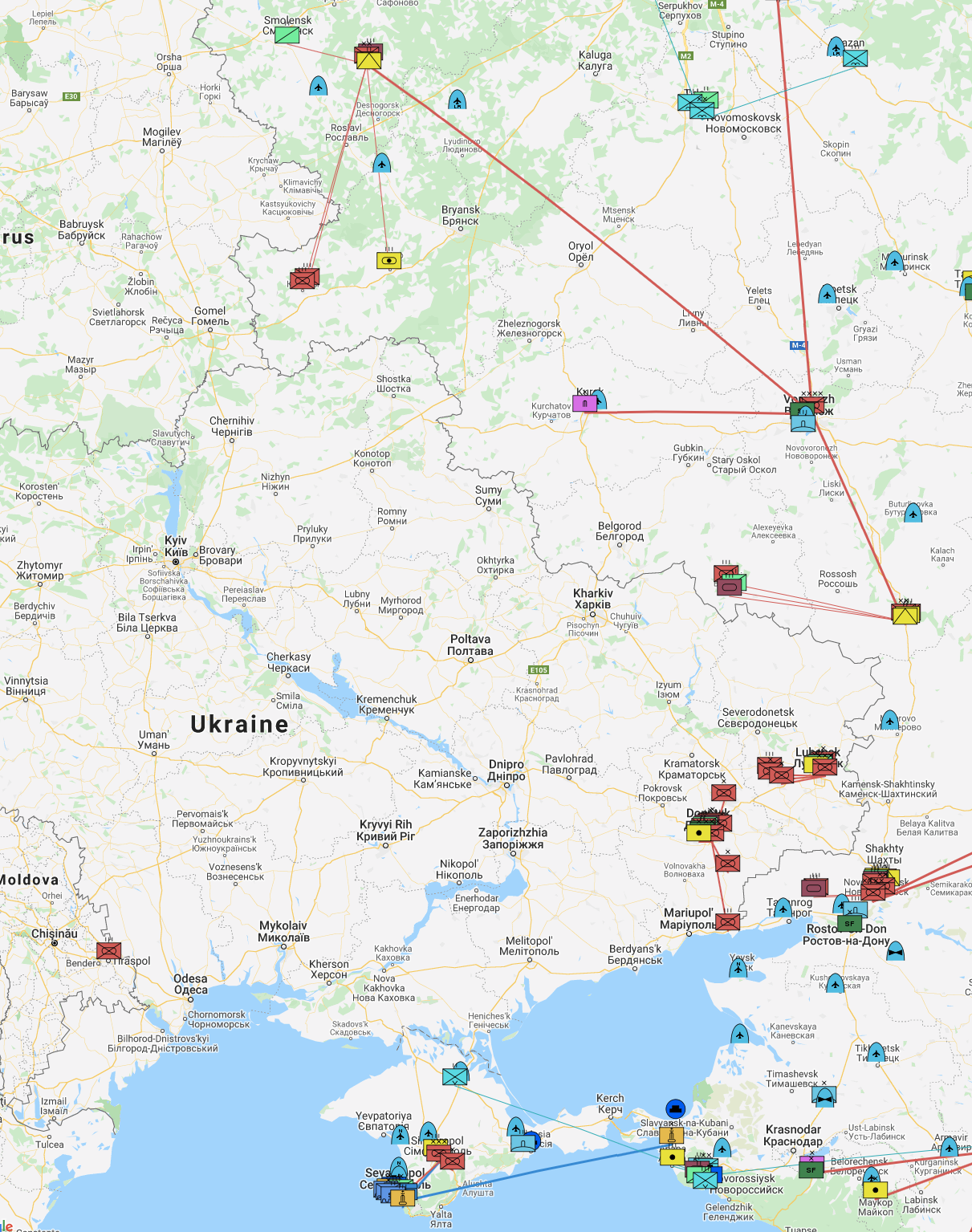
What does it mean? I don't know anything about military strategy, but hazarding a guess is not out of the question. Here is what I would do: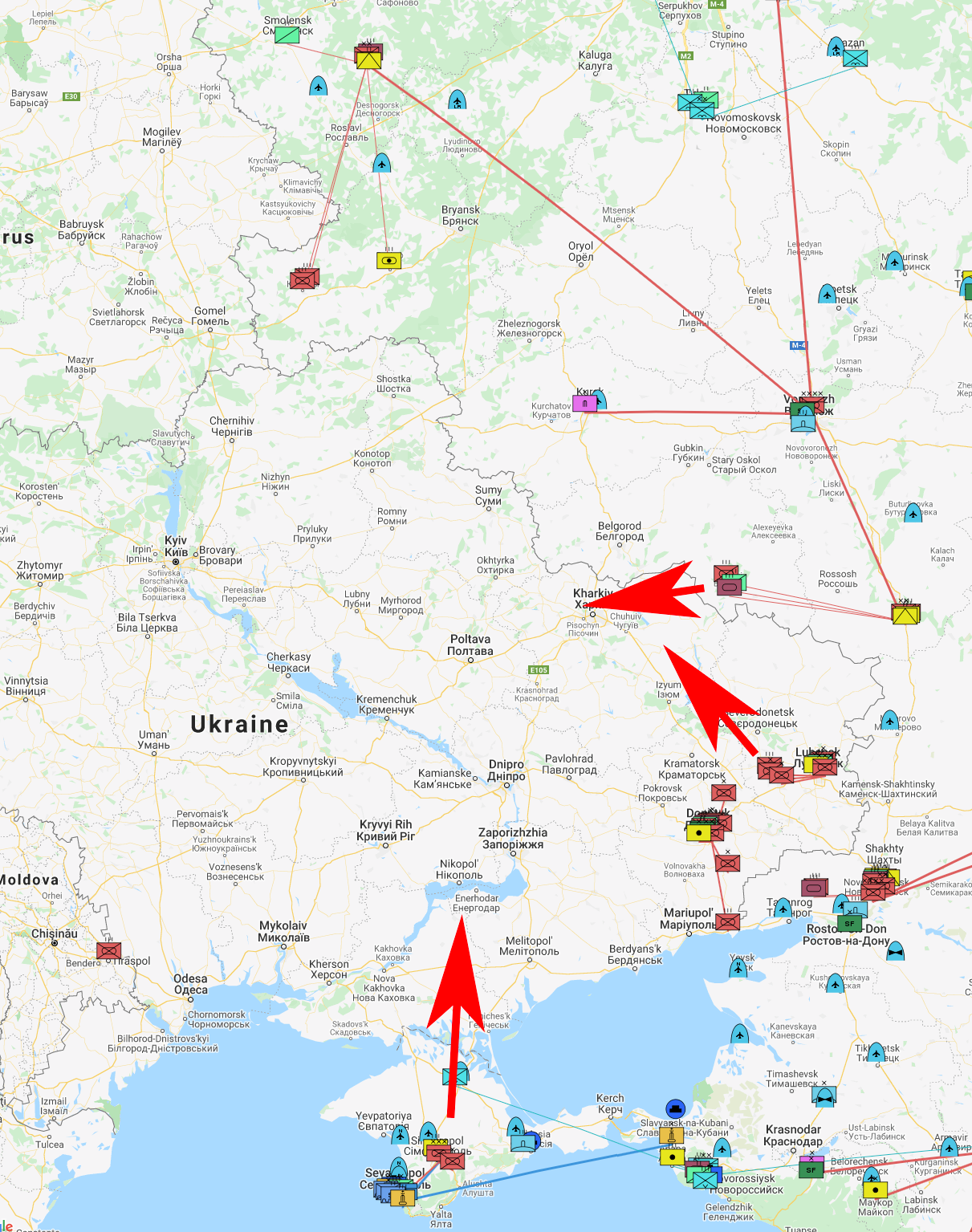
This seems to be supported by a detailed treatment of the subject from March 2018 by the Institute for the Study of War. In the report, the authors argue that Russia is postured for a conventional mechanized invasion of Eastern Ukraine that is supported by Russian doctrine. This was followed by a later report castigating Western nations for failing to counter the hybrid Russian threat of its so-called "special war," with the cover showing unmarked soldiers impersonating local militia the day they took over the Crimean peninsula.
The Cyber Angle
Where to begin? Well, these Russian military bases and forces all have internal web pages and email servers. The logical starting point is mil.ru:
wattersa@Andrews-Mac-mini ~ % dig mil.ru
; <<>> DiG 9.10.6 <<>> mil.ru
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 5667
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;mil.ru. IN A
;; ANSWER SECTION:
mil.ru. 300 IN A 82.202.189.138
;; Query time: 225 msec
;; SERVER: 2001:558:feed::1#53(2001:558:feed::1)
;; WHEN: Thu Apr 22 02:25:42 PDT 2021
;; MSG SIZE rcvd: 51
wattersa@Andrews-Mac-mini ~ % dig mx mil.ru
; <<>> DiG 9.10.6 <<>> mx mil.ru
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42166
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;mil.ru. IN MX
;; ANSWER SECTION:
mil.ru. 300 IN MX 10 mail1.mil.ru.
mil.ru. 300 IN MX 20 mail2.mil.ru.
;; Query time: 224 msec
;; SERVER: 2001:558:feed::1#53(2001:558:feed::1)
;; WHEN: Thu Apr 22 02:26:04 PDT 2021
;; MSG SIZE rcvd: 79
wattersa@Andrews-Mac-mini ~ % whois 82.202.189.138
% IANA WHOIS server
% for more information on IANA, visit http://www.iana.org
% This query returned 1 object
refer: whois.ripe.net
inetnum: 82.0.0.0 - 82.255.255.255
organisation: RIPE NCC
status: ALLOCATED
whois: whois.ripe.net
changed: 2002-11
source: IANA
# whois.ripe.net
inetnum: 82.202.184.0 - 82.202.191.255
netname: RU-KL-20031006
country: RU
org: ORG-KL28-RIPE
admin-c: KLCR1-RIPE
tech-c: KLCR1-RIPE
status: ALLOCATED PA
mnt-by: RIPE-NCC-HM-MNT
mnt-by: KL-MNT
mnt-lower: KDP-MNT
mnt-lower: KL-MNT
mnt-routes: KL-MNT
mnt-routes: KDP-MNT
created: 2017-06-22T11:20:45Z
last-modified: 2017-06-22T11:20:45Z
source: RIPE # Filtered
organisation: ORG-KL28-RIPE
org-name: Kaspersky Lab AO
country: RU
org-type: LIR
address: 39A/3, Leningradskoe Shosse
address: 125212
address: MOSCOW
address: RUSSIAN FEDERATION
phone: +7 495 7978700
fax-no: +7 495 7978700
mnt-ref: RIPE-NCC-HM-MNT
mnt-ref: KL-MNT
mnt-by: RIPE-NCC-HM-MNT
mnt-by: KL-MNT
admin-c: KLCR1-RIPE
admin-c: AP3146-RIPE
admin-c: ZSB5-RIPE
abuse-c: KLCR1-RIPE
created: 2006-09-13T11:06:21Z
last-modified: 2020-12-16T13:03:20Z
source: RIPE # Filtered
role: Kaspersky Lab Contact Role
address: 39A/2 Leningradskoe shosse
address: 125212
address: Moscow
address: RU - Russian Federation
admin-c: AVS140-RIPE
tech-c: AVS140-RIPE
nic-hdl: KLCR1-RIPE
mnt-by: KL-MNT
created: 2006-11-20T14:41:41Z
last-modified: 2015-10-08T11:01:39Z
source: RIPE # Filtered
abuse-mailbox: abuse@kaspersky.com
% Information related to '82.202.189.0/24AS209030'
route: 82.202.189.0/24
origin: AS209030
mnt-by: KDP-MNT
created: 2019-05-13T14:37:27Z
last-modified: 2019-05-13T14:37:27Z
source: RIPE
% This query was served by the RIPE Database Query Service version 1.100 (WAGYU)
wattersa@Andrews-Mac-mini ~ % dig mail1.mil.ru
; <<>> DiG 9.10.6 <<>> mail1.mil.ru
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 30896
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;mail1.mil.ru. IN A
;; ANSWER SECTION:
mail1.mil.ru. 300 IN A 188.128.123.52
;; Query time: 597 msec
;; SERVER: 2001:558:feed::1#53(2001:558:feed::1)
;; WHEN: Thu Apr 22 02:27:36 PDT 2021
;; MSG SIZE rcvd: 57
wattersa@Andrews-Mac-mini ~ % whois 188.128.123.52
% IANA WHOIS server
% for more information on IANA, visit http://www.iana.org
% This query returned 1 object
refer: whois.ripe.net
inetnum: 188.0.0.0 - 188.255.255.255
organisation: Administered by RIPE NCC
status: LEGACY
whois: whois.ripe.net
changed: 1993-05
source: IANA
# whois.ripe.net
inetnum: 188.128.123.32 - 188.128.123.63
netname: RutUb_Moscow
descr: Ticket 09-05348, RISS 7763, MMT
country: RU
admin-c: RTNC-RIPE
tech-c: RTNC-RIPE
status: ASSIGNED PA
mnt-by: ROSTELECOM-MNT
created: 2009-08-17T10:03:11Z
last-modified: 2009-08-17T10:03:11Z
source: RIPE
role: PJSC Rostelecom Technical Team
address: PJSC Rostelecom
address: Russian Federation
abuse-mailbox: abuse@rt.ru
admin-c: DS4715-RIPE
admin-c: EEA-RIPE
admin-c: AV3066-RIPE
tech-c: DS4715-RIPE
tech-c: EEA-RIPE
tech-c: AV3066-RIPE
remarks: trouble: ---------------------------------------------------------------
remarks: trouble: Rostelecom NOC is available 24 x 7
remarks: trouble: e-mail noc-ip@rt.ru
remarks: trouble: ---------------------------------------------------------------
remarks: ------------------------------------------------------------------------
remarks: peering requests: peering@rt.ru
remarks: ------------------------------------------------------------------------
remarks: http://www.rostelecom.ru/, looking-glass http://lg.ip.rt.ru/
remarks: ------------------------------------------------------------------------
nic-hdl: RTNC-RIPE
mnt-by: ROSTELECOM-MNT
created: 2007-11-27T13:28:11Z
last-modified: 2019-01-22T09:16:29Z
source: RIPE # Filtered
% Information related to '188.128.0.0/17AS12389'
route: 188.128.0.0/17
origin: AS12389
descr: ROSTELECOM NETS
mnt-by: ROSTELECOM-MNT
created: 2009-03-12T07:18:04Z
last-modified: 2009-03-12T07:18:04Z
source: RIPE # Filtered
% This query was served by the RIPE Database Query Service version 1.100 (ANGUS)
wattersa@Andrews-Mac-mini ~ %
So, once again, the Ministry of Defense runs its public-facing network through Kaspersky (lol). In case anyone is wondering, I don't care that Kaspersky will see my mapping activity or queries...I'm not doing anything illegal. If anything, more people should do research in this area and publish it so that civilians and the public have a better introduction to the role of Russia as the spoiler on the international stage.
Okay, here is the Border Gateway Protocol routing table for mil.ru when viewed from a publicly available Looking Glass service:
Thu Apr 22 10:59:52.821 UTC
BGP routing table entry for 82.202.189.0/24
Versions:
Process bRIB/RIB SendTblVer
Speaker 2396511621 2396511621
Last Modified: Apr 16 09:41:12.252 for 6d01h
Paths: (2 available, best #1)
Advertised IPv4 Unicast paths to peers (in unique update groups):
38.5.4.117
Path #1: Received by speaker 0
Advertised IPv4 Unicast paths to peers (in unique update groups):
38.5.4.117
20764 209030 209030
149.6.169.218 (metric 110090) from 66.28.1.28 (38.28.1.236)
Origin IGP, metric 0, localpref 140, valid, internal, best, group-best, import-candidate
Received Path ID 0, Local Path ID 1, version 2396511621
Community: 174:140 174:11000 174:20999 174:21101 174:22014
Originator: 38.28.1.236, Cluster list: 66.28.1.28, 66.28.1.9, 66.28.1.3, 38.28.1.123
Path #2: Received by speaker 0
20764 209030 209030
149.6.169.218 (metric 110090) from 154.54.66.21 (38.28.1.236)
Origin IGP, metric 0, localpref 140, valid, internal
Received Path ID 0, Local Path ID 0, version 0
Community: 174:140 174:11000 174:20999 174:21101 174:22014
Originator: 38.28.1.236, Cluster list: 154.54.66.21, 66.28.1.9, 66.28.1.3, 38.28.1.123
When I run the same search on the Data IX looking glass (DataIX is one of the internet exchanges in Karkhiv), I get this table of routes:
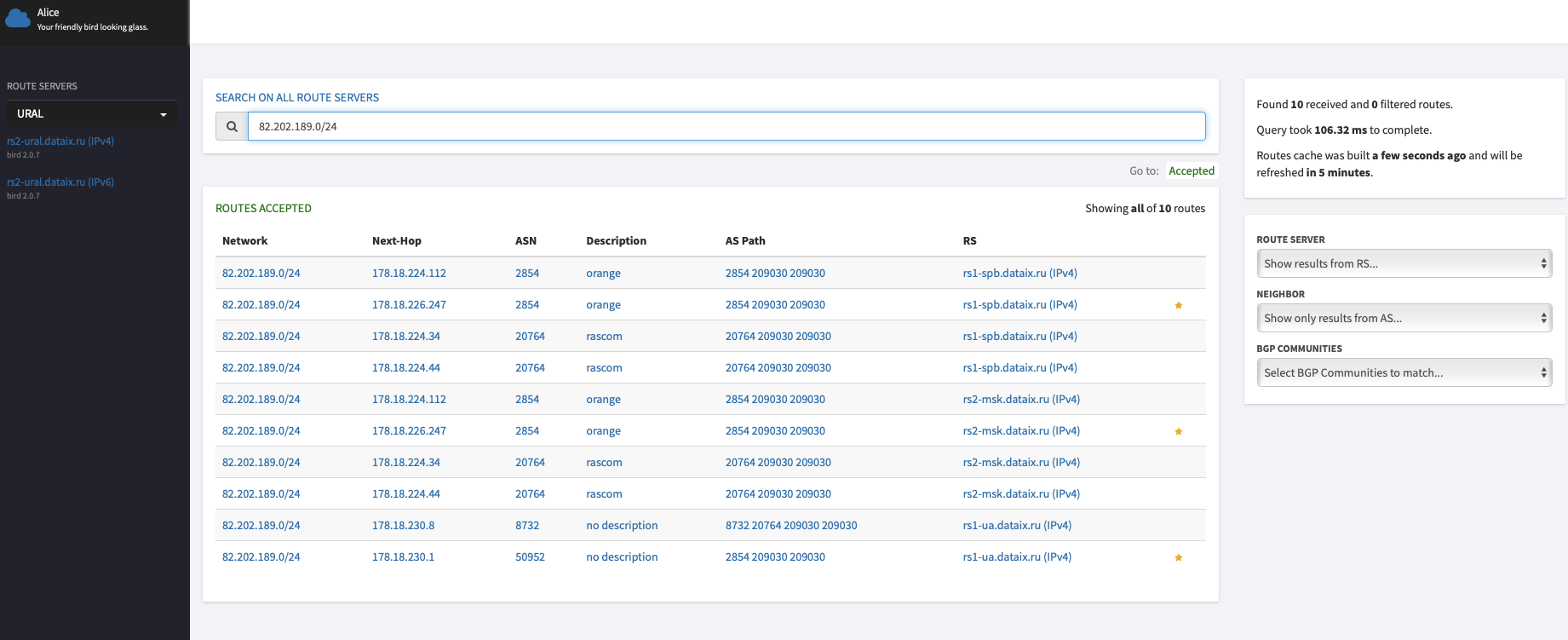
rs1-ua.dataix.ru resolves to 178.18.231.4, which is located in Moscow, so that's one end of the connection. In terms of the actual IP's of the Karkhiv internet exchange, I'm betting the Russians have set up BGP in such a way as to impair the Ukrainian internet in that area in conjunction with an invasion. Working on getting that information...
Update 4/24/2021: Vladimir Putin is either a genius or a madman. I completely bought the idea of a Ukraine invasion and was sure it would happen. He's playing his hand brilliantly, keeping adversaries guessing and accomplishing his goals. That is hybrid war. But now that the world has seen this part of his playbook, what is next?
Update 5/10/2021: 50,000+ page views in the last 90 days...crazy. Another APT is currently trying to hack my server, perhaps triggered by the Ukraine section of this page. They once again tried just enough times to avoid Fail2Ban. I wish there were a way to see what passwords they tried, but enabling logging of failed passwords is usually a bad idea. Here are the relevant lines extracted from my /var/log/secure with my username redacted:
Apr 30 16:51:55 justice sshd[250592]: Failed password for [redacted] from 185.100.87.129 port 54598 ssh2
May 1 15:59:52 justice sshd[265961]: Failed password for [redacted] from 45.153.160.130 port 40245 ssh2
May 1 18:32:03 justice sshd[267706]: Failed password for [redacted] from 104.244.77.101 port 45275 ssh2
May 2 17:40:51 justice sshd[283180]: Failed password for [redacted] from 185.247.224.14 port 39062 ssh2
May 3 04:34:53 justice sshd[290441]: Failed password for [redacted] from 45.153.160.2 port 35132 ssh2
May 3 15:49:17 justice sshd[305690]: Failed password for [redacted] from 45.153.160.138 port 39571 ssh2
May 3 15:57:00 justice sshd[305806]: Failed password for [redacted] from 45.153.160.131 port 40787 ssh2
May 3 20:25:15 justice sshd[309414]: Failed password for [redacted] from 185.220.102.246 port 16242 ssh2
May 5 06:40:13 justice sshd[335800]: Failed password for [redacted] from 18.27.197.252 port 36998 ssh2
May 5 11:12:25 justice sshd[340512]: Failed password for [redacted] from 45.15.16.69 port 19228 ssh2
May 5 15:41:28 justice sshd[345146]: Failed password for [redacted] from 107.189.10.42 port 11506 ssh2
May 5 23:06:46 justice sshd[351389]: Failed password for [redacted] from 45.153.160.130 port 36852 ssh2
May 6 00:42:46 justice sshd[352532]: Failed password for [redacted] from 23.129.64.203 port 27617 ssh2
May 6 18:52:26 justice sshd[369910]: Failed password for [redacted] from 185.220.103.4 port 40416 ssh2
May 6 21:28:00 justice sshd[371592]: Failed password for [redacted] from 23.129.64.251 port 58085 ssh2
May 7 02:08:36 justice sshd[374569]: Failed password for [redacted] from 23.129.64.251 port 17272 ssh2
May 7 06:37:46 justice sshd[377599]: Failed password for [redacted] from 185.56.80.65 port 47178 ssh2
May 7 09:01:14 justice sshd[379422]: Failed password for [redacted] from 192.187.111.130 port 34366 ssh2
May 7 23:59:42 justice sshd[391953]: Failed password for [redacted] from 185.191.124.152 port 41464 ssh2
May 8 07:39:00 justice sshd[396806]: Failed password for [redacted] from 162.247.74.201 port 51306 ssh2
May 8 22:28:50 justice sshd[406620]: Failed password for [redacted] from 91.132.147.168 port 59830 ssh2
May 9 00:33:19 justice sshd[407908]: Failed password for [redacted] from 185.247.224.14 port 37757 ssh2
May 9 02:57:56 justice sshd[409692]: Failed password for [redacted] from 91.149.225.120 port 33130 ssh2
May 9 18:20:27 justice sshd[419197]: Failed password for [redacted] from 23.129.64.239 port 46725 ssh2
May 9 23:34:57 justice sshd[422523]: Failed password for [redacted] from 23.129.64.231 port 13685 ssh2
Update 7/15/2021: I think they gave up after two months. Lol.
Update 2/4/2022: A few months ago I added new firewall rules to only allow SSH from certain locations, which was intended to end the hacking campaigns I have experienced. It appears to have had the desired effect, though I have not fully analyzed the webserver and email server logs yet. This was an interesting experience and I collected plenty of data, which means I now have to go back and analyze all of it (lol). I'm intending to finish this page at some point, so feel free to check back in over the next couple of months. Thanks to all my visitors (>200,000 so far from all over the world).
Update 2/5/2022: Analysis of mail server and webserver logs indicates that several of the above addresses from April/May 2021 were still active in trying to hack me from late 2021 to now (February 2022), even though I disabled SSH for almost the entire internet. A couple of the addresses resolve to non-profit security organizations, while others go to the Seychelles and the Netherlands. I'll have to cross reference these potential APT's with my firewall logs to see whether there is any overlap. It's in progress. One interesting technique has been using the GeoIP library to do a first pass on the logs so I can cut down the number of IP's I need to check. Check out this one-liner that I came up with, and the results:
[[redacted] ~]$ let count=0; while read line; do let count=(count + 1); echo "Line: $count IP: $line"; geoiplookup $line; done < access.txt | grep -B 1 Russia
Line: 237 IP: 195.201.166.168
GeoIP Country Edition: RU, Russian Federation
--
Line: 269 IP: 212.192.246.107
GeoIP Country Edition: RU, Russian Federation
--
Line: 566 IP: 77.88.5.40
GeoIP Country Edition: RU, Russian Federation
Line: 567 IP: 77.88.5.50
GeoIP Country Edition: RU, Russian Federation
--
Line: 612 IP: 93.158.161.33
GeoIP Country Edition: RU, Russian Federation
Line: 613 IP: 93.158.161.58
GeoIP Country Edition: RU, Russian FederationIt's interesting because the GeoIP result doesn't always match the WHOIS information. The first address above traces to Germany, for example. Looks like I need to go back over my original logs and run GeoIP on all the entries to see where the IP's really go, haha.
What's even more interesting is that many of the IP's in the presumed APT list above do not resolve at all in GeoIP...check this out:
[[redacted] syn]$ let count=0; while read line; do let count=(count + 1); echo "Line: $count IP: $line"; geoiplookup $line; done < APT
Line: 1 IP: 185.100.87.129
GeoIP Country Edition: RO, Romania
Line: 2 IP: 45.153.160.130
GeoIP Country Edition: IP Address not found
Line: 3 IP: 104.244.77.101
GeoIP Country Edition: US, United States
Line: 4 IP: 185.247.224.14
GeoIP Country Edition: IP Address not found
Line: 5 IP: 45.153.160.2
GeoIP Country Edition: IP Address not found
Line: 6 IP: 45.153.160.138
GeoIP Country Edition: IP Address not found
Line: 7 IP: 45.153.160.131
GeoIP Country Edition: IP Address not found
Line: 8 IP: 185.220.102.246
GeoIP Country Edition: IP Address not found
Line: 9 IP: 18.27.197.252
GeoIP Country Edition: US, United States
Line: 10 IP: 45.15.16.69
GeoIP Country Edition: IP Address not found
Line: 11 IP: 107.189.10.42
GeoIP Country Edition: US, United States
Line: 12 IP: 45.153.160.130
GeoIP Country Edition: IP Address not found
Line: 13 IP: 23.129.64.203
GeoIP Country Edition: IP Address not found
Line: 14 IP: 185.220.103.4
GeoIP Country Edition: IP Address not found
Line: 15 IP: 23.129.64.251
GeoIP Country Edition: IP Address not found
Line: 16 IP: 23.129.64.251
GeoIP Country Edition: IP Address not found
Line: 17 IP: 185.56.80.65
GeoIP Country Edition: NL, Netherlands
Line: 18 IP: 192.187.111.130
GeoIP Country Edition: US, United States
Line: 19 IP: 185.191.124.152
GeoIP Country Edition: IP Address not found
Line: 20 IP: 162.247.74.201
GeoIP Country Edition: US, United States
Line: 21 IP: 91.132.147.168
GeoIP Country Edition: GR, Greece
Line: 22 IP: 185.247.224.14
GeoIP Country Edition: IP Address not found
Line: 23 IP: 91.149.225.120
GeoIP Country Edition: PL, Poland
Line: 24 IP: 23.129.64.239
GeoIP Country Edition: IP Address not found
Line: 25 IP: 23.129.64.231
GeoIP Country Edition: IP Address not foundUpdate 2/25/2022: Obviously, a lot is going on with the Ukraine invasion and I intend to update this page in the near future. What a dark day for Europe, as I have been discussing on Twitter. I am working on a concept plan and some policy documents on Russia as part of my Congressional campaign. FYI, I put ads on the page as a test of whether it's worth doing ads; my colocation costs a substantial amount each month and I currently give away everything else on my websites for free, so it seems fair. But feedback is welcome.
Update 6/8/2022: I deleted the ads because Google AdSense is simply not worth doing. I'd rather make nothing than $0.50 for hundreds of page views, haha. Updates coming soon.
Work in progress.
© 2024 Andrew G. Watters
Last updated: June 08, 2022 19:00:52
Telemetry: page generated in 0.1 milliseconds for user at 18.217.3.94 on 2024-10-21 23:48:05